Summary
When the Advanced TLS Traffic Inspection feature is enabled on Red Hat Enterprise Linux 7 with SELinux enforcing mode, the TLS inspection feature cannot work because BPF operations such as map_create are denied by the SELinux default policy.
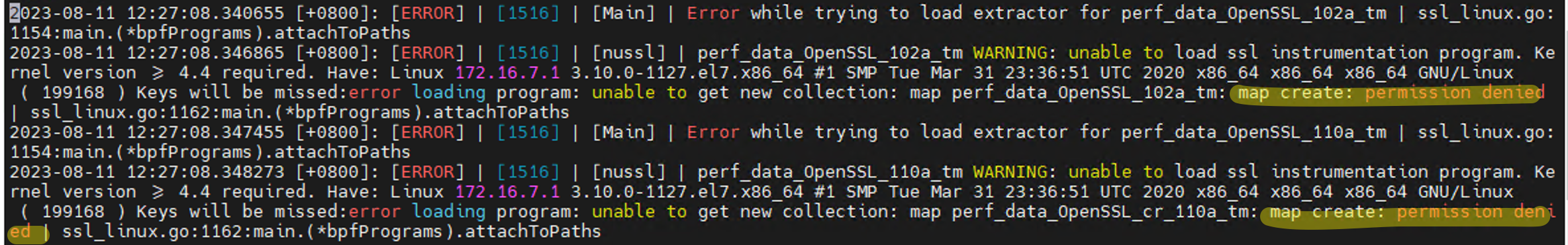
The alert might appear in the system log or SELinux log (/var/log/audit/audit.log or /var/log/audit.log):
type=AVC msg=audit(1682773485.952:1080): avc: denied { map_create } for pid=12807 comm="ds_nuagent" scontext=system_u:system_r:unconfined_service_t:s0 tcontext=system_u:system_r:unconfined_service_t:s0 tclass=bpf permissive=0
type=SYSCALL msg=audit(1682773485.952:1080): arch=c000003e syscall=321 success=no exit=-13 a0=0 a1=c000a25800 a2=2c a3=0 items=0 ppid=12802 pid=12807 auid=4294967295 uid=0 gid=0 euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=(none) ses=4294967295 comm="ds_nuagent" exe="/opt/ds_agent/nuagent/ds_nuagent" subj=system_u:system_r:unconfined_service_t:s0 key=(null)
type=PROCTITLE msg=audit(1682773485.952:1080): proctitle=2F6F70742F64735F6167656E742F6E756167656E742F64735F6E756167656E74002D2D64656275670073736C002D2D6465627567006D61696E002D2D6465627567006B657973002D2D6465627567006E75746170002D2D6465627567006E756167656E74636C69656E74002D2D646562756700646F636B6572002D2D64656275
The Advanced TLS Traffic Inspection feature does not work on Red Hat Enterprise Linux 7 (64-bit) starting Deep Security Agent (DSA) 20.0.0-7119 when SELinux is enabled with enforcing mode.
Below are the root causes:
- We introduced ds_nuagent self-protection support for security enhancement since DSA 20.0.0-7119.
- The ds_nuagent security context then changed from init_t to unconfined_service_t which doesn't have BPF operation permission such as map_create.
- There is an SELinux bugfix on the later policy version 3.14 to extend unconfined_service_t permission for BPF operations.
As a workaround, add a custom SELinux rule to allow BPF operations for unconfined_service_t context:
- Create a custom policy: create a file named "nuagent.te" with the following contents:
module nuagent 1.0;
require {
type unconfined_service_t;
class bpf { map_create map_read map_write prog_load prog_run };
}
#============= unconfined_service_t ==============
allow unconfined_service_t self:bpf { map_create map_read map_write prog_load prog_run };
- Check the policy and generate a module named "nuagent.mod".
checkmodule -M -m -o nuagent.mod nuagent.te
- Create an SELinux policy module package named "nuagent.pp".
semodule_package -o nuagent.pp -m nuagent.mod
- Insert the custom policy.
semodule -i nuagent.pp
- Restart ds_nuagent by restarting ds_agent.
systemctl restart agent
FAQs
- How do I confirm that the permission issue is resolved?
Before applying the fix, you will see error logs about the permission issue in /var/opt/ds_agent/nuagent/ds_nuagent-err.log. When this is fixed you will not see similar logs.
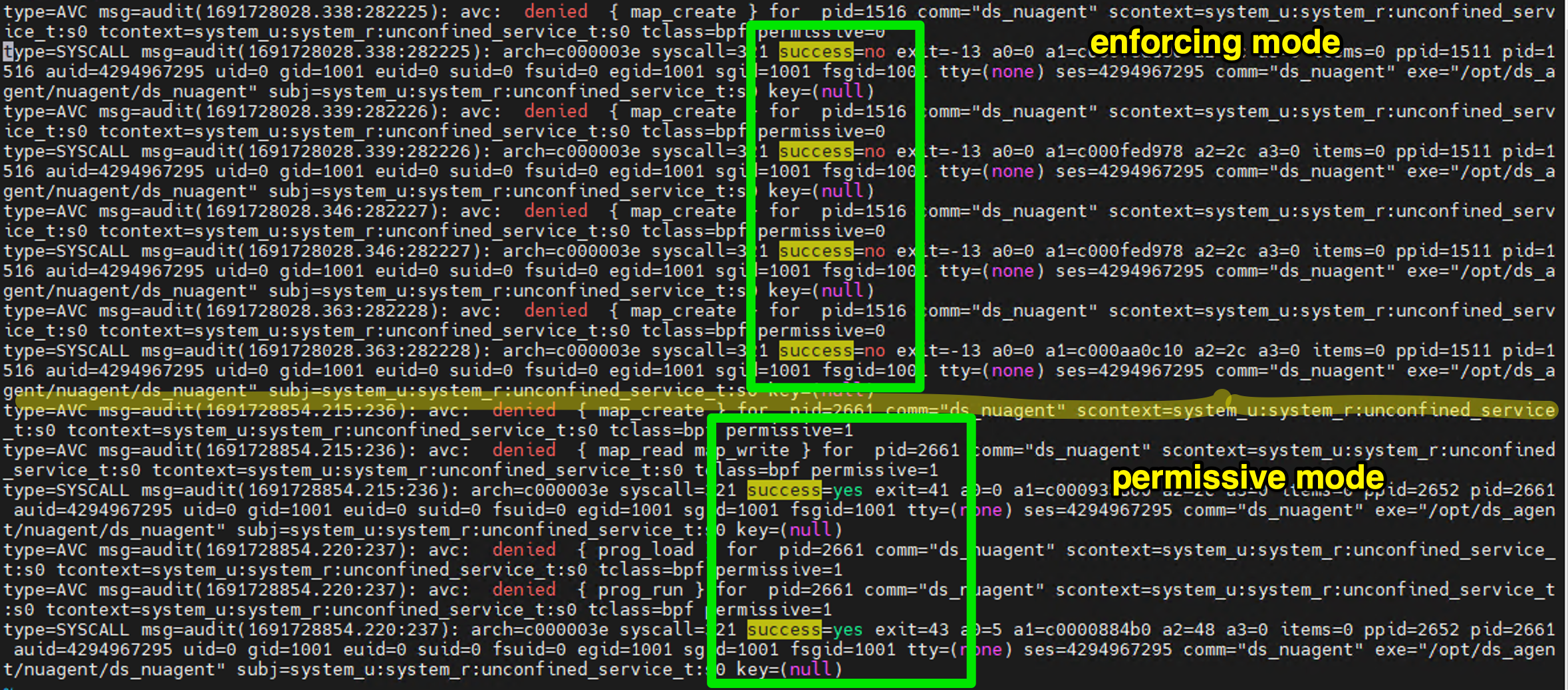
- Does SELinux permissive mode have this permission issue?
No. You will see the audit log but the function is working.
- What will happen if the fix is not applied?
The only impact is Advanced TLS traffic inspection.
- Does the permission issue impact other security modules and Self-Protection?
No. This issue will not impact other security modules and Self-Protection.


