General Product Operation
Server & Workload Protection, by design, does not collect personal information. When a security event occurs, information about the event is transferred to Trend Micro. Depending on the nature of the protected environment and the object that is the target of the security event (for example, files, memory, network traffic) there is a risk that personal information may be collected within a security event. Security policy configuration and module selection are provided to meet the requirements of your target environment and minimize this risk. The default event retention period for Server & Workload Protection is 32 days.
| General Product Operation (Modules) |
|---|
| Data Collected | Security event information:- Anti-Malware
- For cloud query:
- For detection log:
- File name
- File path
- Suspicious process data
- Container information
- User name
- Domain
- Full process path
- For exclusion list:
- File path
- File directory
- Full file path
- For uploaded files:
- Web Reputation
- For cloud query:
- URL
- IP address
- Endpoint name
- User name
- For prevention of browser exploitation:
- Suspicious URLs
- HTTP headers or HTML files from suspicious URLs
- Browser information
- For exclusion list:
- Device Control
- For detection log:
- Target file
- Process accessing device
- USB device
- Device type
- Name
- Vendor
- Model
- Serial number
- For exclusion list:
- Name
- Vendor
- Model
- Serial number
- Application Control
- For detection log:
- Rule name
- RuleSet name
- File name
- File path
- Number of repetitions
- User name
- User ID
- Process name
- Process ID
- For exclusion list:
- Full update or installer program path
- File name
- File path
- Firewall
- For custom rules:
- Rule name
- Rule description
- Rule configuration
- For detection log:
- Rule name
- Interface
- Source IP address
- Source port
- Source MAC address
- Destination IP address
- Destination port
- Destination MAC address
- Intrusion Prevention
- For custom rules:
- Rule name
- Rule description
- Rule configuration
- For detection log:
- Rule name
- Interface
- Source IP address
- Source Port
- Source MAC address
- Destination IP address
- Destination Port
- Destination MAC address
- Suspicious process data
- Container information
- Packet data
- Integrity Monitoring
- For custom rules:
- Rule name
- Rule description
- Rule configuration (FileSet, DirectorySet, ServiceSet, UserSet, GroupSet, PortSet, Processes,
RegistryKeySet, RegistryValueSet, WQLSet)
- For detection log:
- Rule name
- Rule modification
- Rule description
- Process name
- User name
- Log Inspection
- For custom rules:
- Rule name
- Rule description
- Rule configuration
- Decoder name
- Decoder description
- Decoder configuration
- For detection log:
- Rule name
- Rule description
- Group
- Location
- Source IP address
- Source port
- Destination IP address
- Destination port
- Protocol
- Action
- Source user
- Destination user
- Event
- Host name
- Original event
- ID
- Status
- Command
- URL
- Data
- System name
- Associated rule
- Event origin
|
|---|
| Console Location | Computer or Policy editor > Select module (e.g. Anti-Malware, Web Reputation, etc) |
|---|
| Console Settings | State: Off or Inherited (Off) 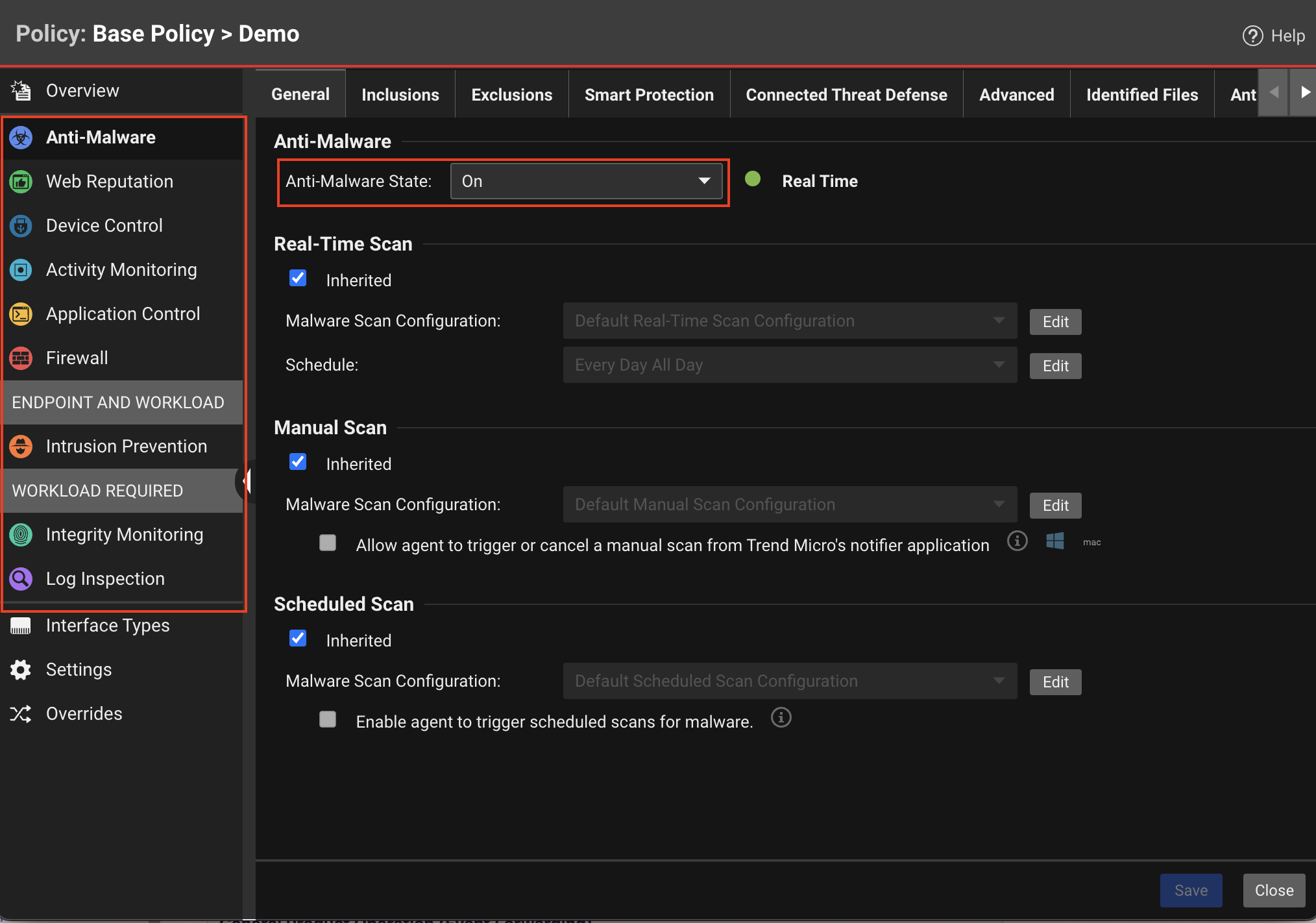
|
|---|
| General Product Operation (Event Forwarding) |
|---|
| Data Collected | Security event information:- Intrusion prevention packet
- URL reputation
- Firewall packet
- Log entry
- Malware file
- IP addresses
- Mobile and USB device blocked logs
|
|---|
| Console Location | Administration > System Settings > Event Forwarding |
|---|
| Console Settings | - Forward System Events to a remote computer (via Syslog) using configuration
- Publish Events to AWS Simple Notification Service
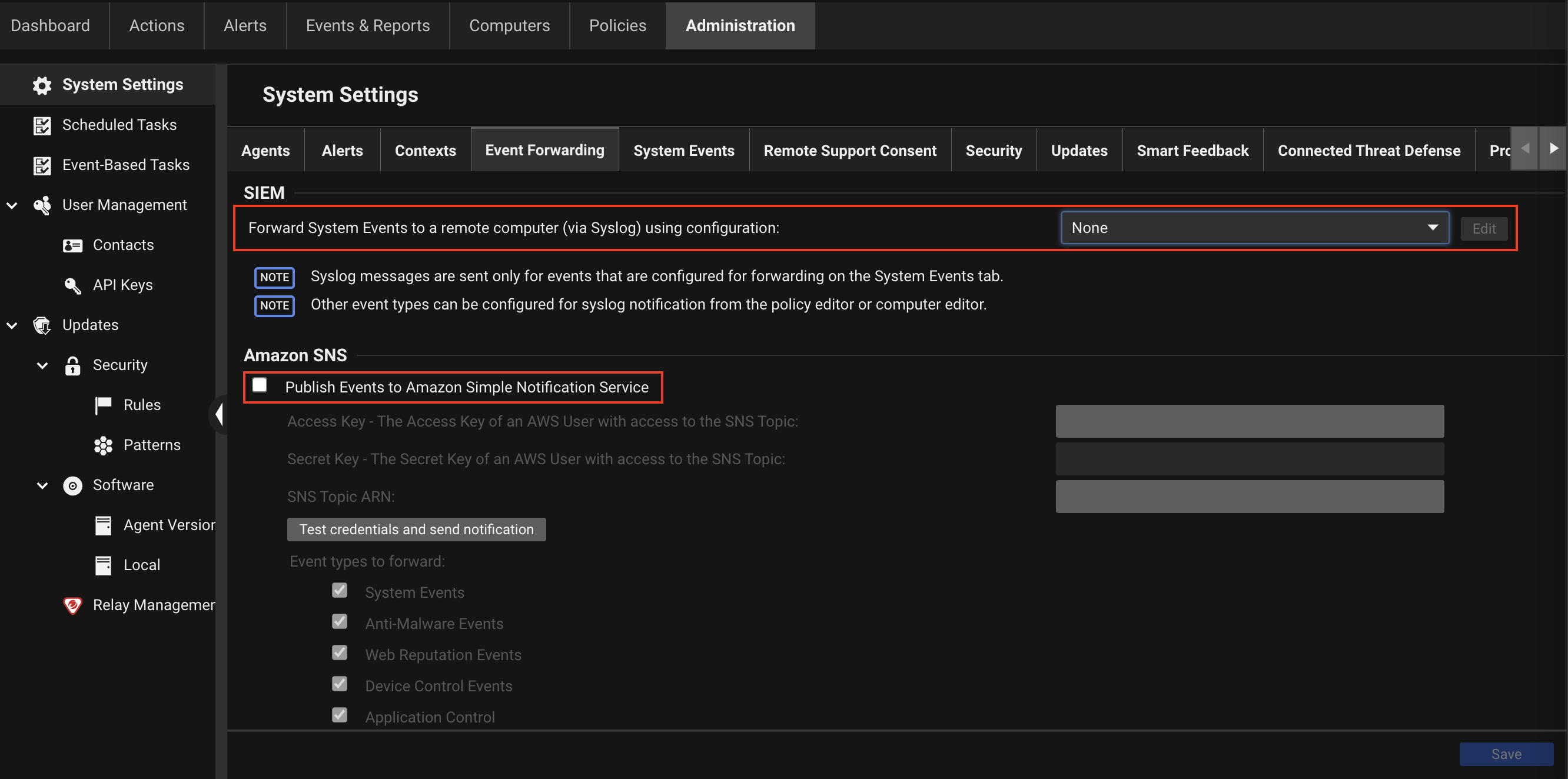
|
|---|
| General Product Operation (Logging and Monitoring) |
|---|
| Data Collected | Data from AWS ELB and other logs, including:- Names
- Email addresses
- Session IDs
- IP addresses
- CloudWatch logs
- Server0 entries
- HTTP traffic
|
|---|
| Console Location | This information is stored in the Server & Workload Protection SIEM and is used for troubleshooting, monitoring, and overall protection of the system. It cannot be configured or disabled by customer. |
|---|
Contact Email
Server & Workload Protection transmits reports, alerts, and registration confirmation to its email server when sending this information to customers.
| Email Configuration (Contacts) |
|---|
| Data Collected | - Reports
- Alerts
- Registration confirmation
|
|---|
| Console Location | Administration > User Management > Contacts |
|---|
| Console Settings | Email Address 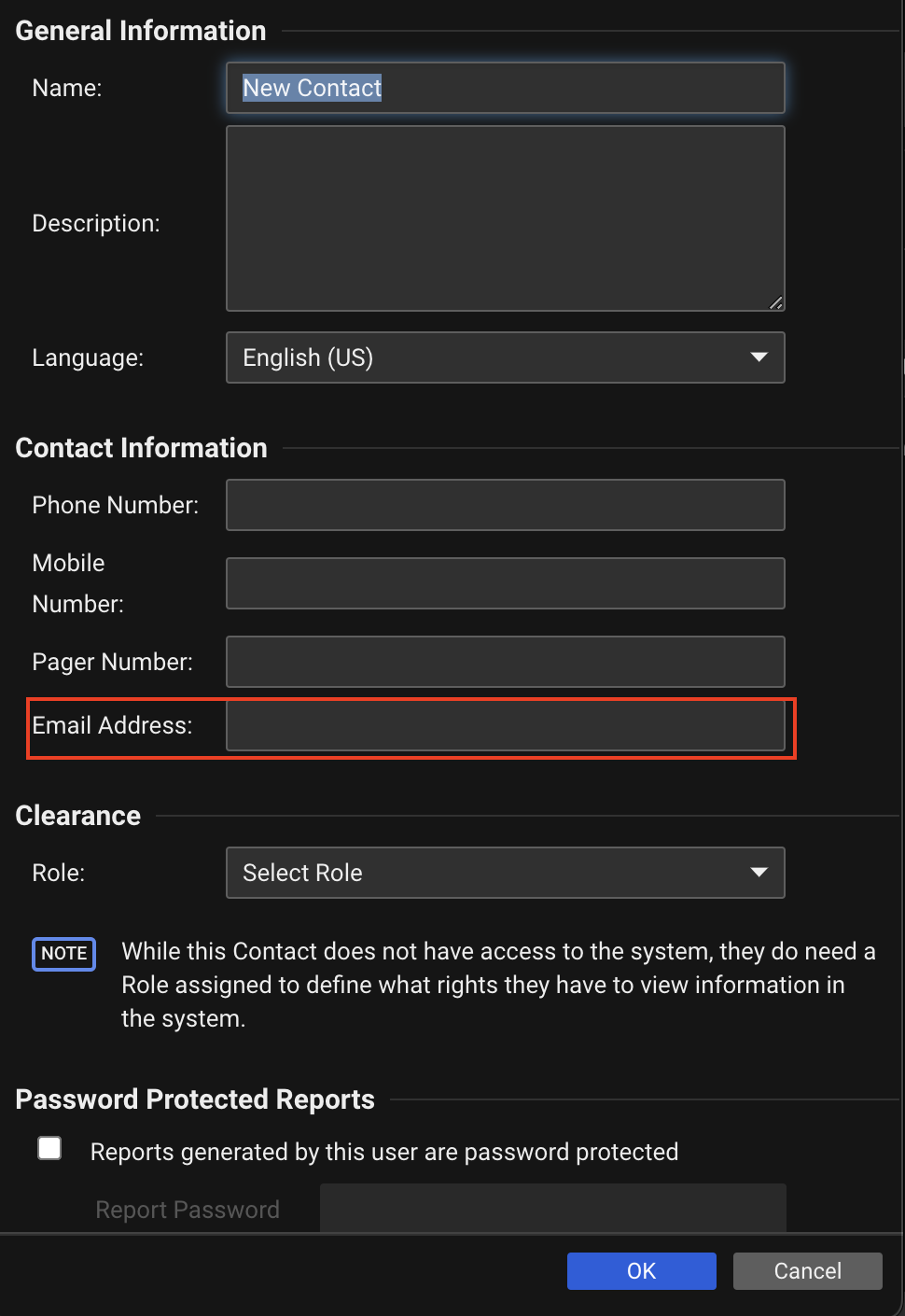
This contact information will show up when configuring Scheduled Reports under Generate Reports.
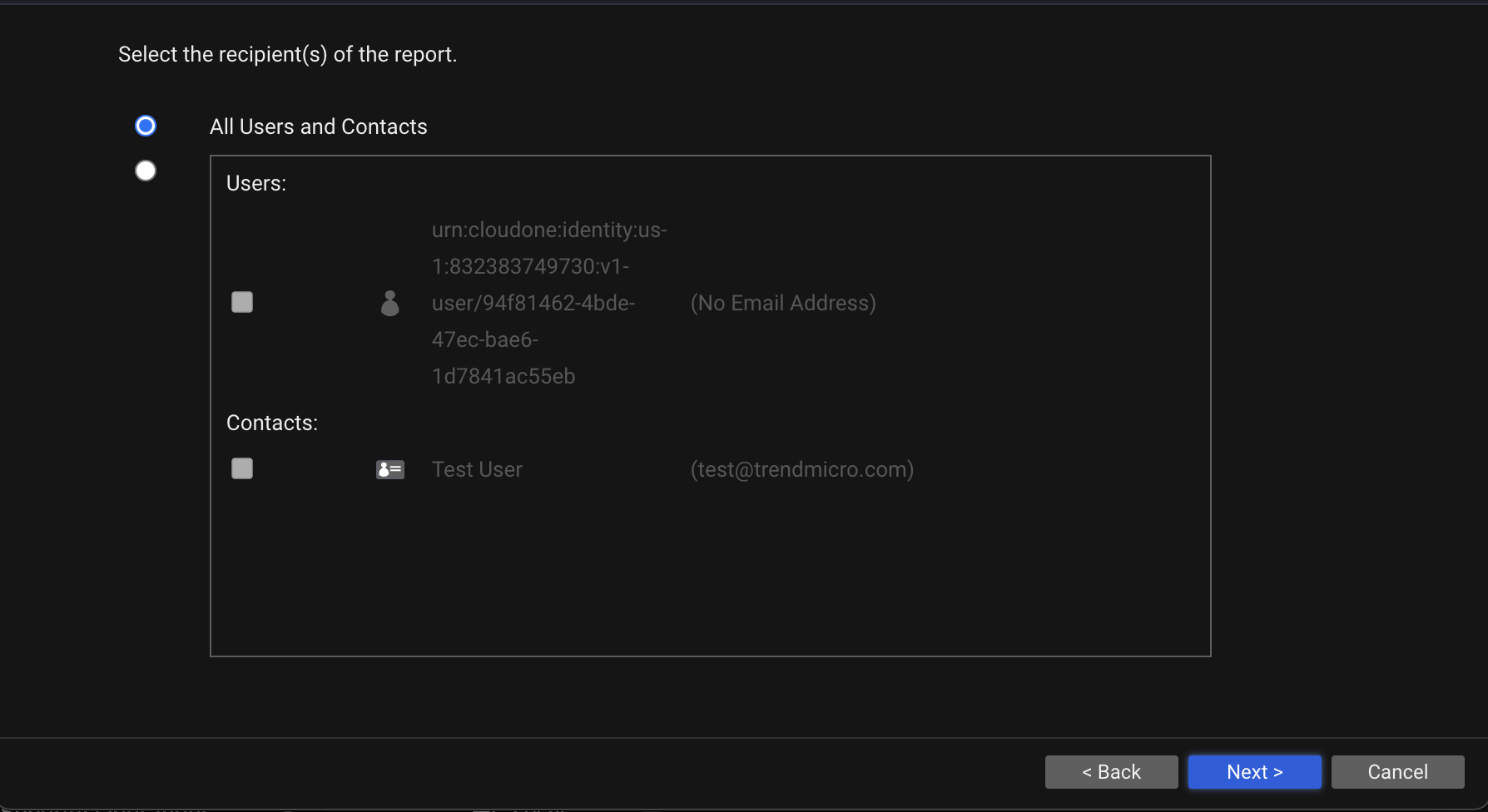
|
|---|
Endpoint Management
| Trend Micro Endpoint Basecamp |
|---|
| Description | Trend Micro Endpoint Basecamp is a lightweight agent that serves as the control & deployment & upgrade channel for Trend Vision One Endpoint Security.
If you do not want to allow Trend Micro to collect these data items, do not install the agent program.
|
|---|
| Data Collected | - Endpoint GUID
- Endpoint name
- Endpoint IP address
- MAC address
|
|---|
| Console Location | Not configurable using the web console |
|---|
| Trend Vision One Endpoint Security Telemetry Agent |
|---|
| Description | Trend Vision One Endpoint Security Telemetry Agent helps Trend Micro gather diagnostic telemetry for proactively identify technical issues for better improving the stability and performance of Trend Vision One Endpoint Security.
If you do not want to allow Trend Micro to collect these data items, do not install the agent program.
|
|---|
| Data Collected | - Endpoint GUID
- IP Address
- File name/path*
- Process name/path*
- Trend Vision One Endpoint Security program file versions
- Trend Vision One Endpoint Security program settings
- Trend Vision One Endpoint Security performance data
- Windows file versions
- Windows performance data
*Some of the collected information may contain Personally Identifiable Information (PII). |
|---|
| Console Location | Not configurable using the web console |
|---|
Endpoint Sensor
| Trend Vision One Endpoint Sensor: Attack Surface Discovery |
|---|
| Description | Attack Surface Discovery collects detail operating system configuration and installed applications metadata periodically to perform risk assessment and present the risk event & score in Risk Insights. |
|---|
| Data Collected | - Endpoint GUID
- OS SKU, detail version & patch history
- Installed Application records
- Registry data
|
|---|
| Console Location | Endpoint Security Operations > Endpoint Inventory |
|---|
| Console Settings | Not configurable using the web console |
|---|
| Trend Vision One Endpoint Sensor: Detection and Response |
|---|
| Description | Trend Vision One Endpoint Sensor is a powerful monitoring and investigation tool used to identify the presence, location, and entry point of threats. Through the use of detailed system event recording and correlation with threat intel, you can perform effective investigations to discover hidden threats throughout your network, locate all affected endpoints, and remediate swiftly. |
|---|
| Data Collected | - Endpoint GUID
- Endpoint name
- IP address
- User name
- Process command line
- Process owner
- File name & full path
- File owner
- File signer
- URL
- Registry data
- Windows event log
|
|---|
| Console Location | Endpoint Security Operations > Endpoint Inventory |
|---|
| Console Settings | 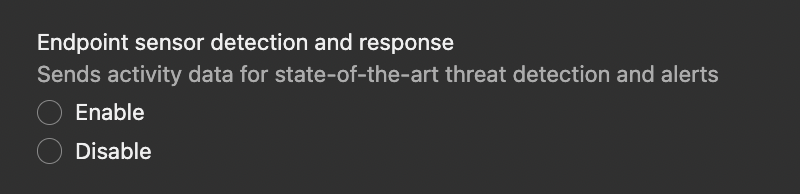
|
|---|
| Trend Vision One Endpoint Sensor: Advanced Risk Telemetry |
|---|
| Description | Advanced Risk Telemetry helps to identify attack surfaces including vulnerabilities related to 3rd party applications more accurately and timely on top of regular Attack Surface Discovery. |
|---|
| Data Collected | - Endpoint GUID
- Process command line
- Service metadata
- File name & full path
|
|---|
| Console Location | Endpoint Security Operations > Endpoint Inventory |
|---|
| Console Settings | 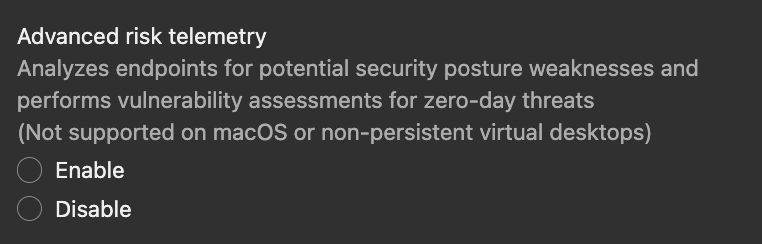
|
|---|
Intrusion Prevention and Firewall
| Description | You can optionally configure Server & Workload Protection to use a Whois service to look up which domain name is associated with an IP address when you review logged intrusion prevention and firewall events. The IP address is sent directly to the Whois service and not to Trend Micro. |
|---|
| Data Collected | |
|---|
| Console Location | Administration > System Settings > Advanced |
|---|
| Console Settings | Whois URL 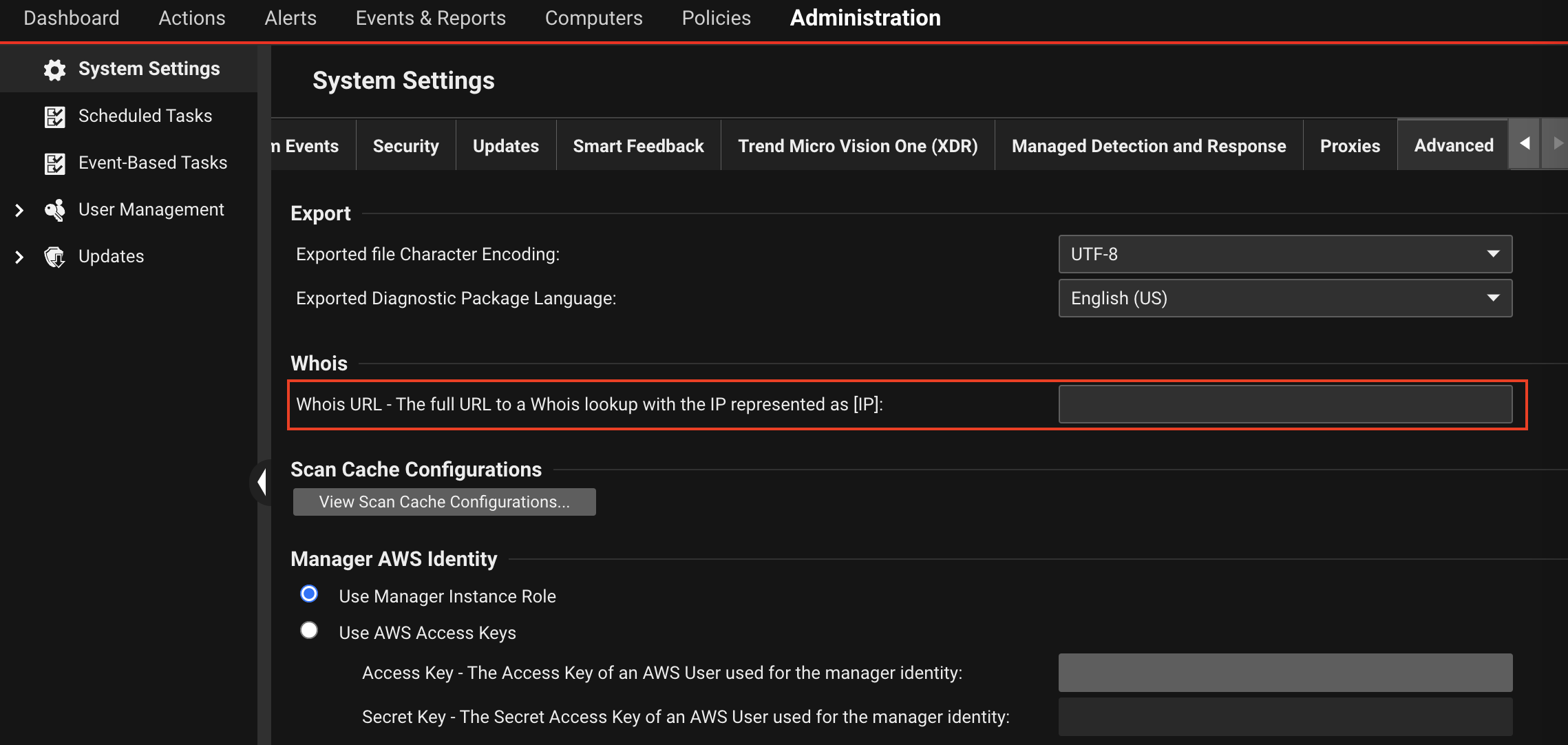
|
|---|
Anti-Malware: Smart Protection
| Description | Smart Protection Server for File Reputation Service is used by the anti-malware module. It supplies file reputation information required by Smart Scan. Alternatively, you can use a locally installed Smart Protection Server. |
|---|
| Data Collected | - Product information
- Client device OS
- Malicious or suspicious file information
- Suspicious file signatures
- Malicious or suspicious process information
|
|---|
| Console Location | Computer or Policy editor > Anti-Malware > Smart Protection |
|---|
| Console Settings | Connect directly to Global Smart Protection Service 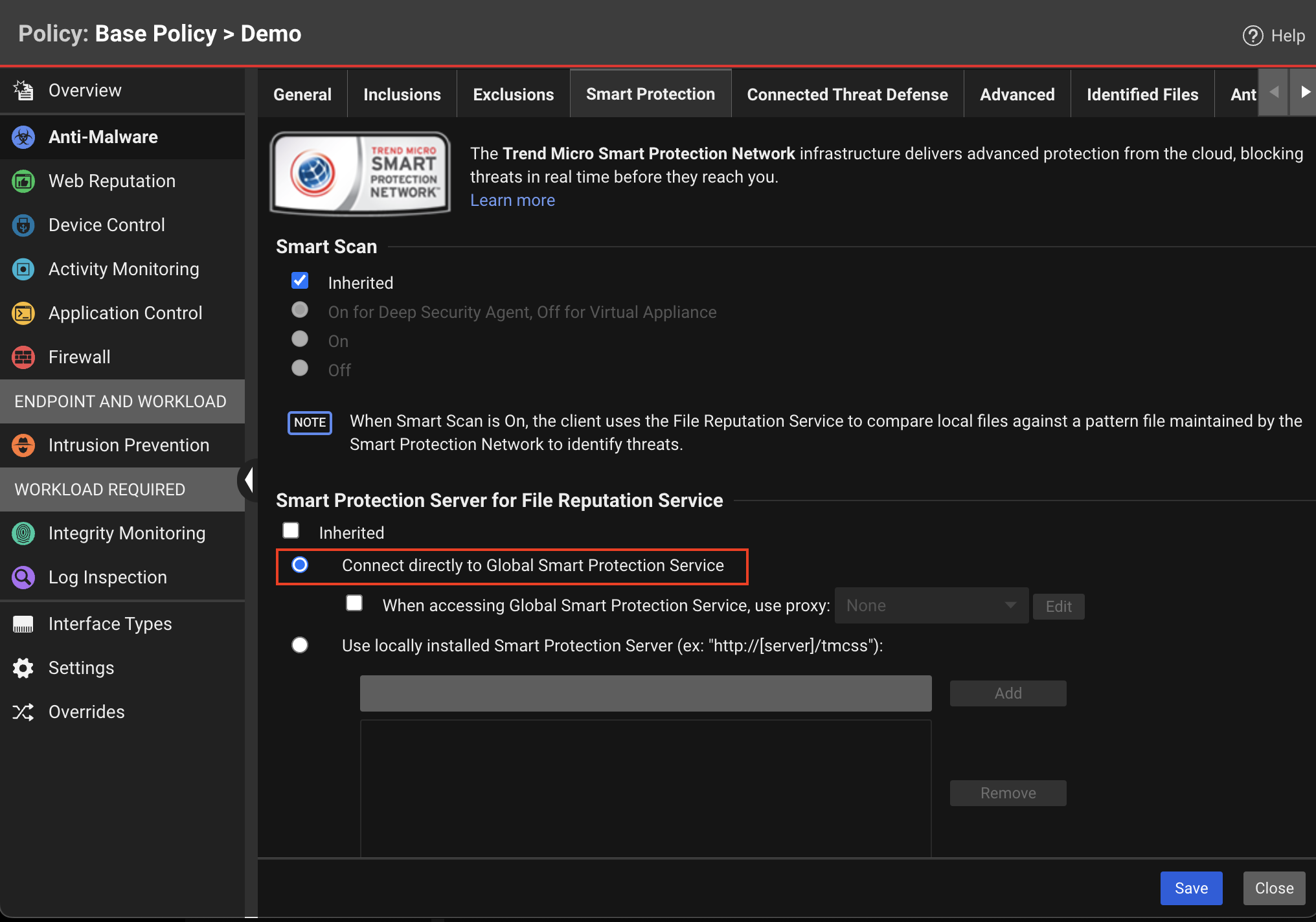
|
|---|
Anti-Malware: Process Memory Scan
| Description | Process Memory Scan connects to the Good File Reputation Service. This information enables Server & Workload Protection to identify good file hashes. |
|---|
| Data Collected | |
|---|
| Console Location | Policies > Common Object > Other > Malware Scan Configurations > Real-Time Scan configuration > General |
|---|
| Console Settings | Scan process memory for malware 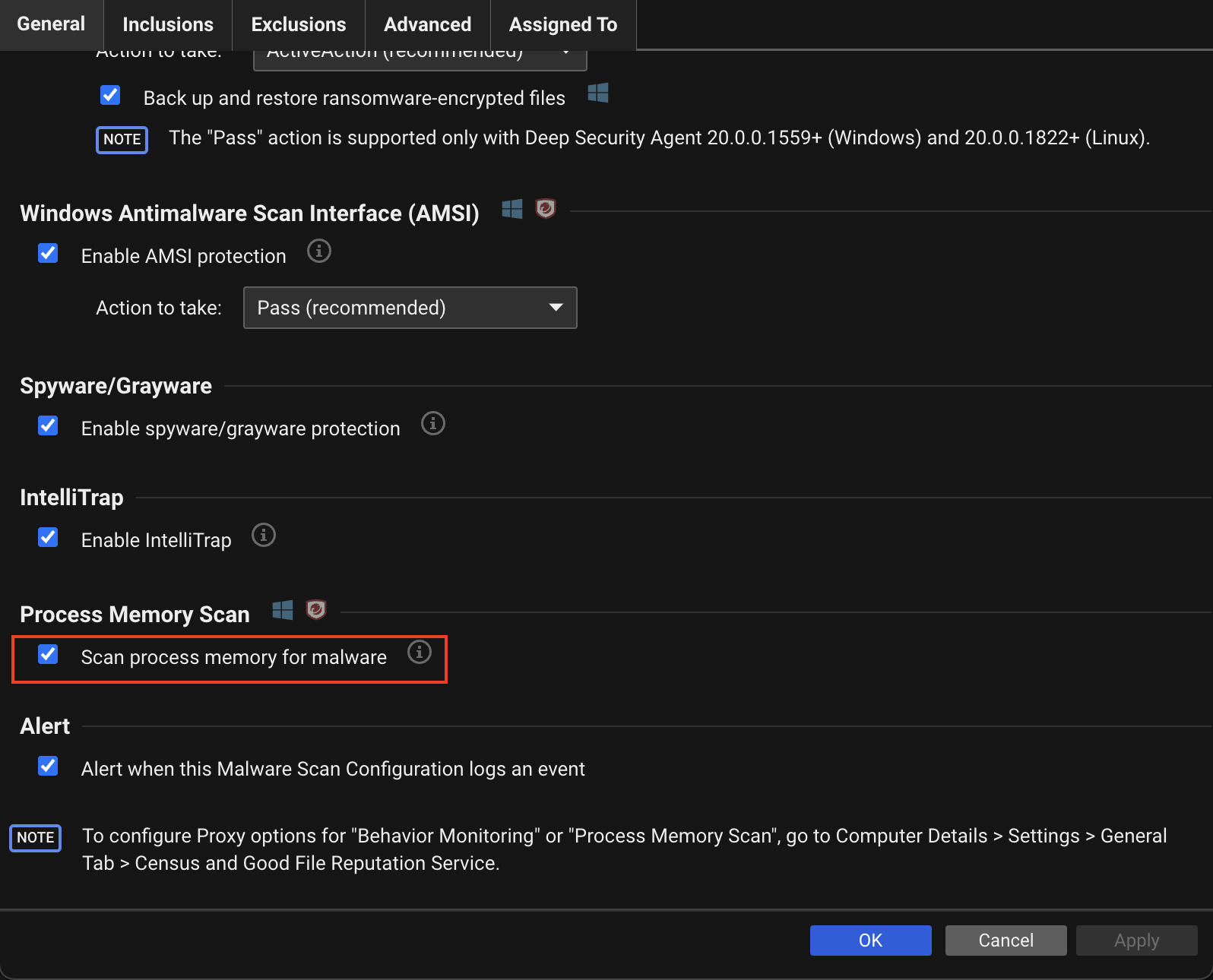
|
|---|
Anti-Malware: Predictive Machine Learning
| Description | Predictive Machine Learning enables identification of potential malicious files. |
|---|
| Data Collected | - For cloud query:
- File name
- File path
- Digital signer
- Process data
- For detection log:
- File name
- File path
- Suspicious process data
- Container information
- User name
- Domain
- Full process path
- For exclusion list:
- File path
- File directory
- Full file path
- For uploaded files:
|
|---|
| Console Location | Policies > Common Objects > Other > Malware Scan Configurations > Real-Time Scan configuration > General |
|---|
| Console Settings | Enable Predictive Machine Learning 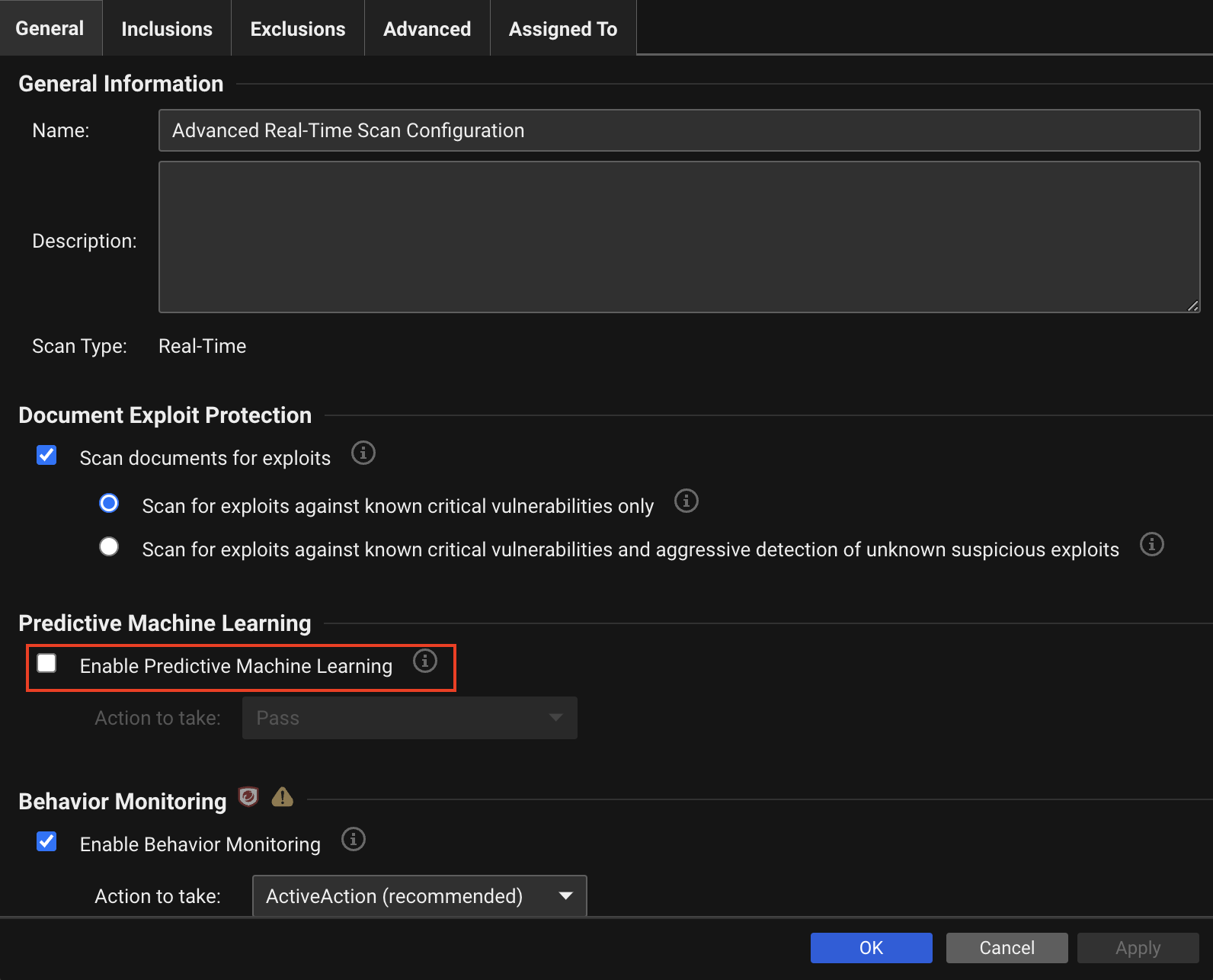
|
|---|
Anti-Malware: Smart Scan
| Description | This information is sent when a file scan occurs and enables Server & Workload Protection to identify malicious file hashes. |
|---|
| Data Collected | |
|---|
| Console Location | Computer or policy editor > Anti-Malware > Smart Protection > Smart Scan |
|---|
| Console Settings | Untick Inherited check box (if it's selected) and select Off. 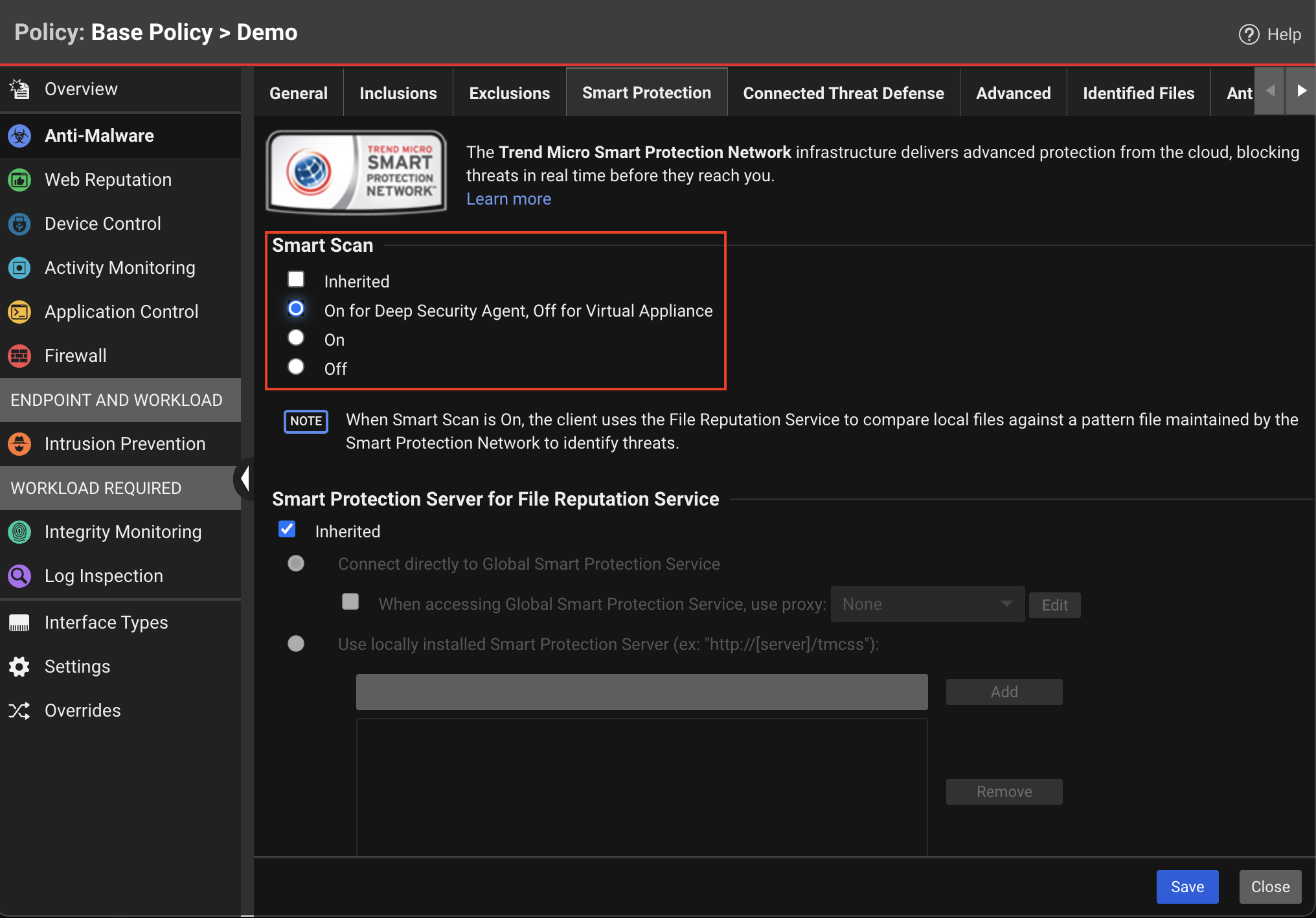
|
|---|
Anti-Malware: Behavior Monitoring
| Description | The behavior monitoring feature communicates with the Global Census Server and Good File Reputation Service. This enables Server & Workload Protection to identify good file hashes and to retrieve statistical data. |
|---|
| Data Collected | - For cloud query:
- For detection log:
- File name
- File path
- Suspicious process data
- Container information
- User name
- Domain
- Full process path
- For exclusion list:
- For uploaded files:
|
|---|
| Console Location | Policies > Common Objects > Other > Malware Scan Configuration > Real-Time Scan configuration > General |
|---|
| Console Settings | - Detect suspicious activity and unauthorized changes (incl. ransomware)
- Back up and restore ransomware-encrypted files
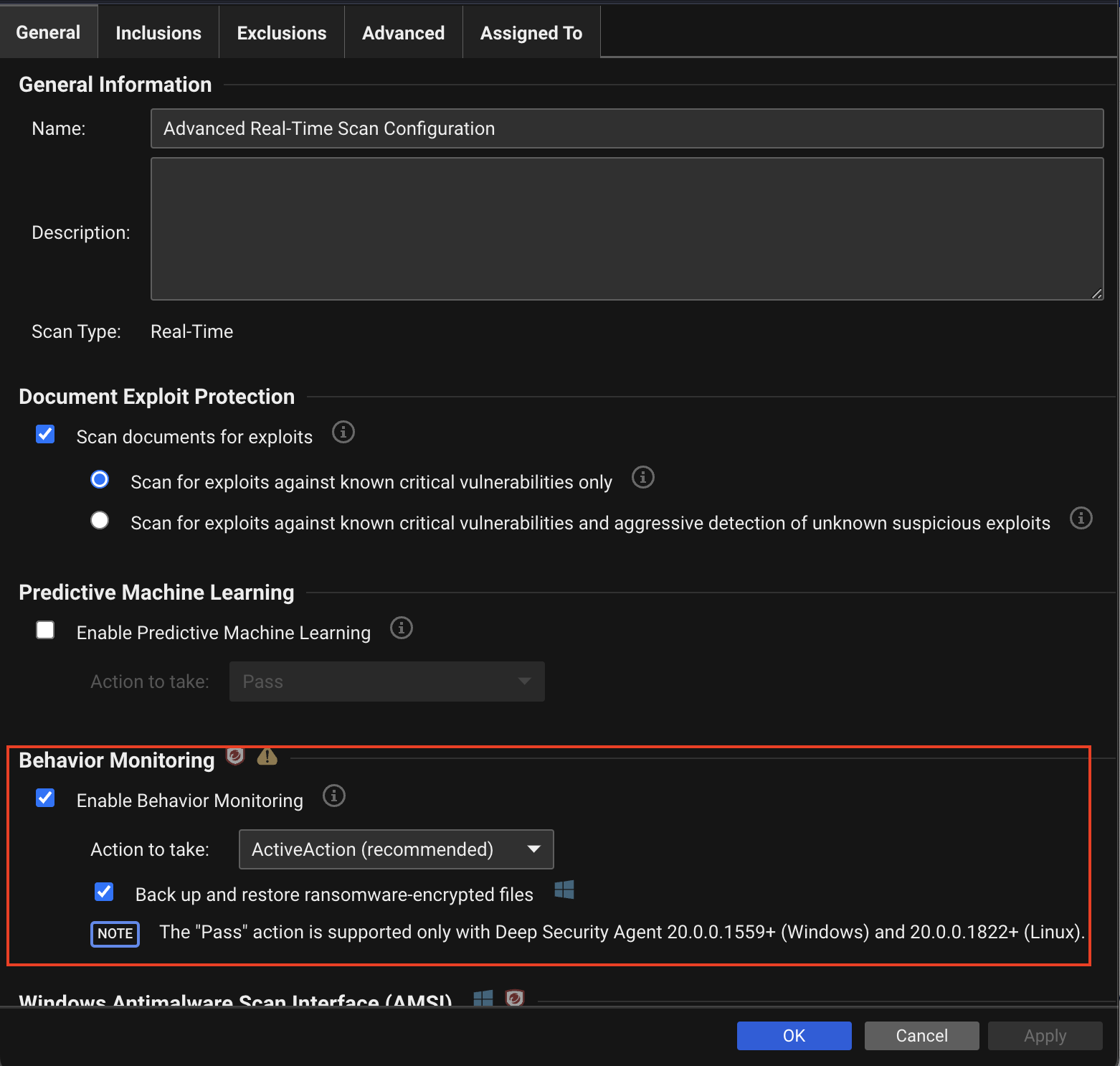
|
|---|
Anti-Malware: Identified (Quarantined) Files
| Description | An identified file is a file that has been found to be or to contain malware and has therefore been encrypted and moved to a special folder on the protected computer. Identified files are not sent to Server & Workload Protection unless you specifically download them using the actions described below. |
|---|
| Data Collected | - Files that have been identified as potential malware
|
|---|
| Console Location | Events & Reports > Events > Anti-Malware Events > Identified Files |
|---|
| Console Settings | The file is sent to Server & Workload Protection only if you select it and click Download. |
|---|
Integrity Monitoring
| Description | You can configure Server & Workload Protection to automatically tag integrity monitoring events. If you select the Certified Safe Software Service option, information is sent to the Trend Micro Certified Safe Software service. Alternatively, you can select one of the other options when configuring auto tagging, or don’t enable auto-tagging. |
|---|
| Data Collected | - File hashes (SHA1) and additional information
|
|---|
| Console Location | Events and Reports > Integrity Monitoring Events > Auto-Tagging > New Trusted Source |
|---|
| Console Settings | Certified Safe Software Service 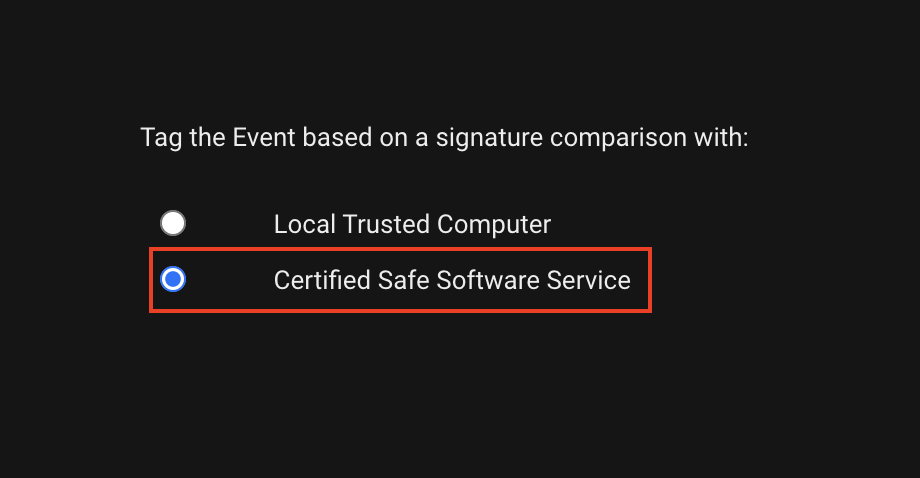
|
|---|
Web Reputation
| Description | The web reputation module uses the Trend Micro Smart Protection Network to determine whether URLs are malicious. When Connect directly to Global Smart Protection Service is selected, URLs are sent to Trend Micro. Alternatively, you can opt to use a locally installed Smart Protection Server. You must select one of these options to use the web reputation module. If you don’t want to use either of those options, go to the General tab and change the Web Reputation State to Off to disable the web reputation module. |
|---|
| Data Collected | |
|---|
| Console Location | Computer or Policy editor > Web Reputation > Smart Protection |
|---|
| Console Settings | Connect directly to Global Smart Protection Service 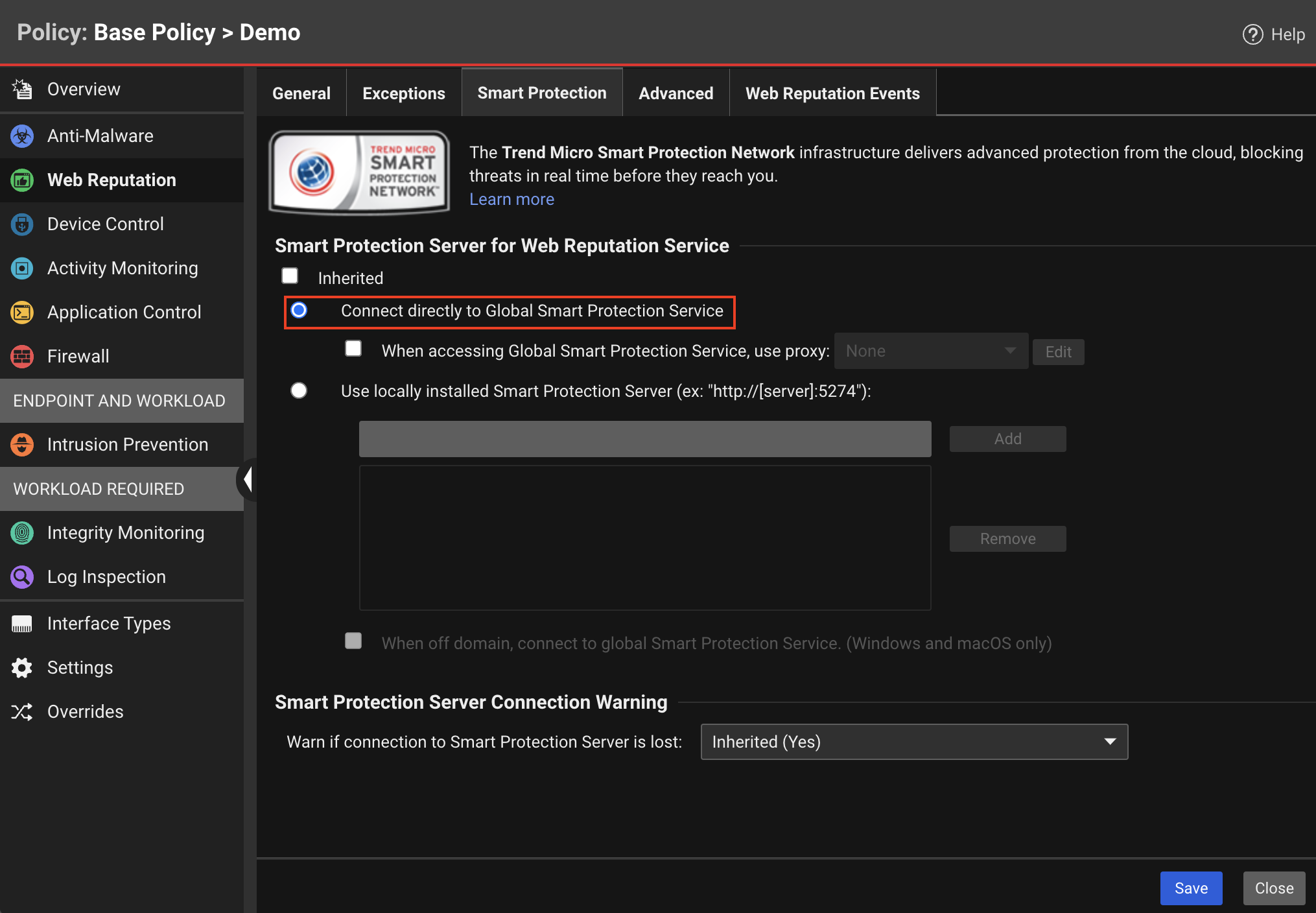
|
|---|
Activity Monitoring
| Description | Activity Monitoring is a protection policy that enables security-related activity to be sent to Trend Micro Security Operations, providing effective expert analytics and global threat intelligence using data collected across multiple vectors - email, endpoints, servers, cloud workloads, and networks.
Activity Monitoring data is only sent to Trend Micro if the server has the Activity Monitoring policy assigned and state of the policy is On. |
|---|
| Data Collected | - Tenant GUID
- Account name
- Process activity
- File activity
- Network activity
- Registry activity (Windows only)
- Connection activity
- Domain query activity
- User account activity (Windows only)
- Modified process activity
- Memory activity
- Behavior monitoring activity
|
|---|
| Console Location | Computer or Policy editor > Activity Monitoring > General > Activity Monitoring State: On |
|---|
| Console Settings | 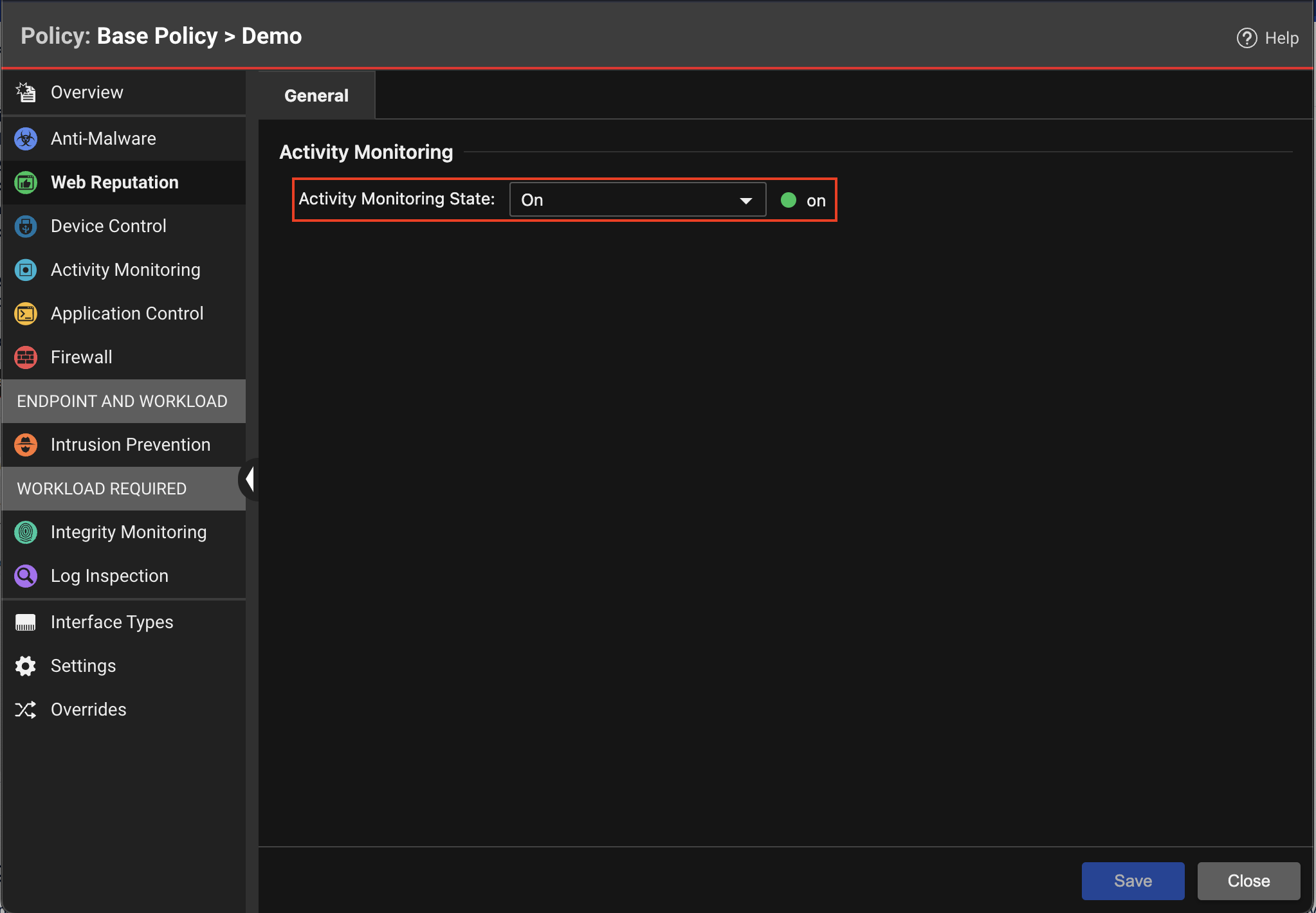
|
|---|
Data Center Gateway Registration
| Description | When you register a new Data Center Gateway on Server & Workload Protection, an identifiable name and optional description will be collected for future reference. The information that you provided may or may not refer to your data-center name or its location.
Data Center Gateway is required only for deployments that Add a VMware vCenter accounts to Cloud One Workload Security. https://cloudone.trendmicro.com/docs/workload-security/vcenter-add/ |
|---|
| Data Collected | - Data Center Gateway Name
- Data Center Gateway Description
|
|---|
| Console Location | System Settings > Data Center Gateway > New |
|---|
| Console Settings | 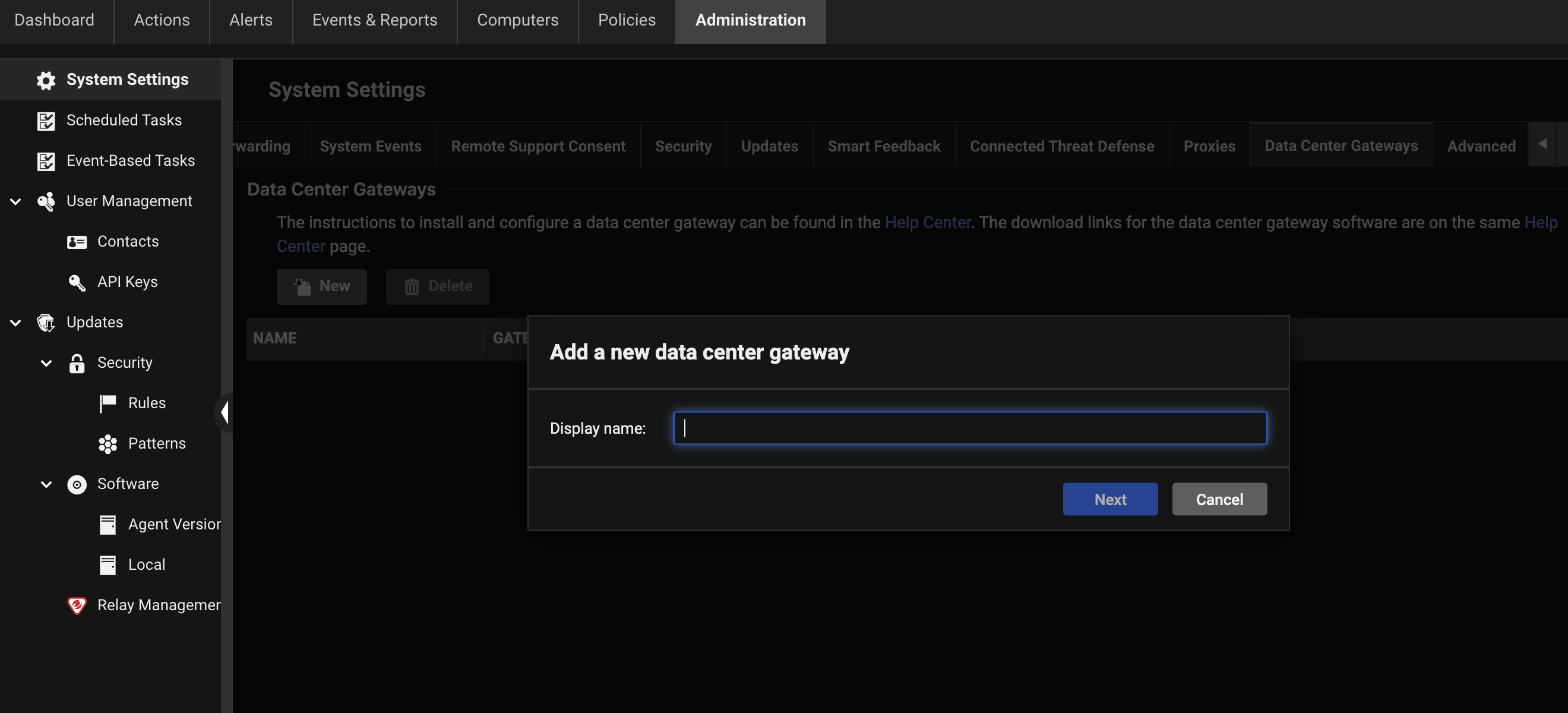
|
|---|
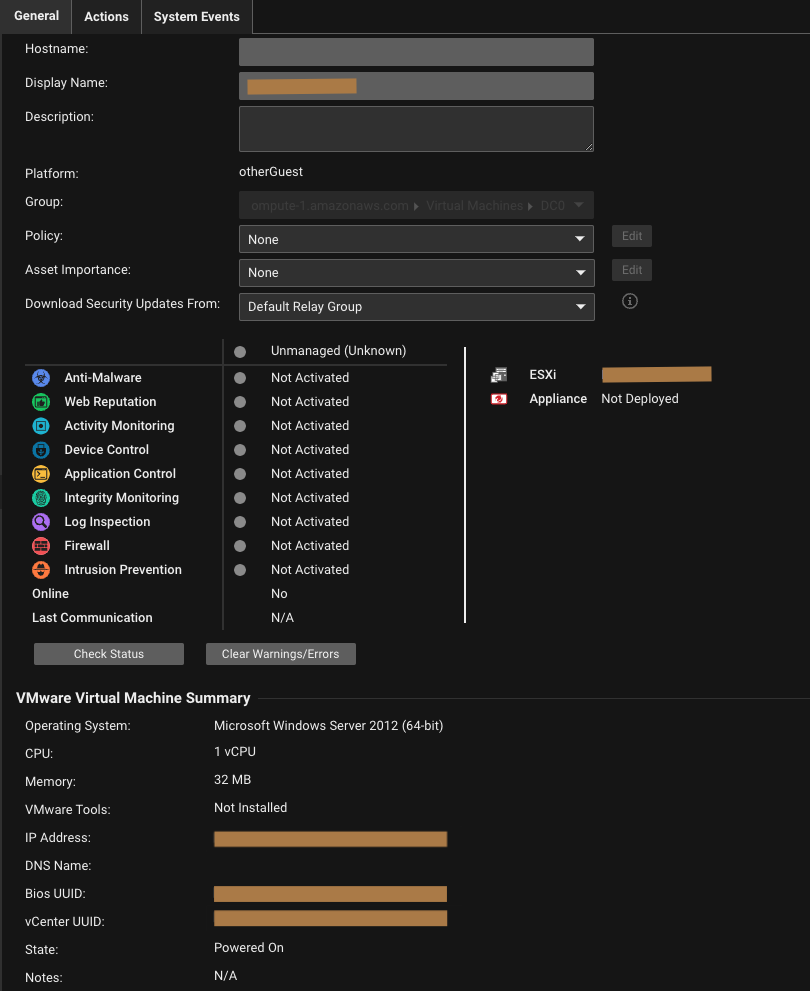
VMware vCenter Registration
| Description | When you add a VMware vCenter account on Server & Workload Protection, the following data is stored and encrypted in order to synchronize the virtual machine data from vCenter servers. |
|---|
| Data Collected | - vCenter Server Address
- vCenter Server Port
- vCenter Credential
|
|---|
| Console Location | Computers > Add |
|---|
| Console Settings | 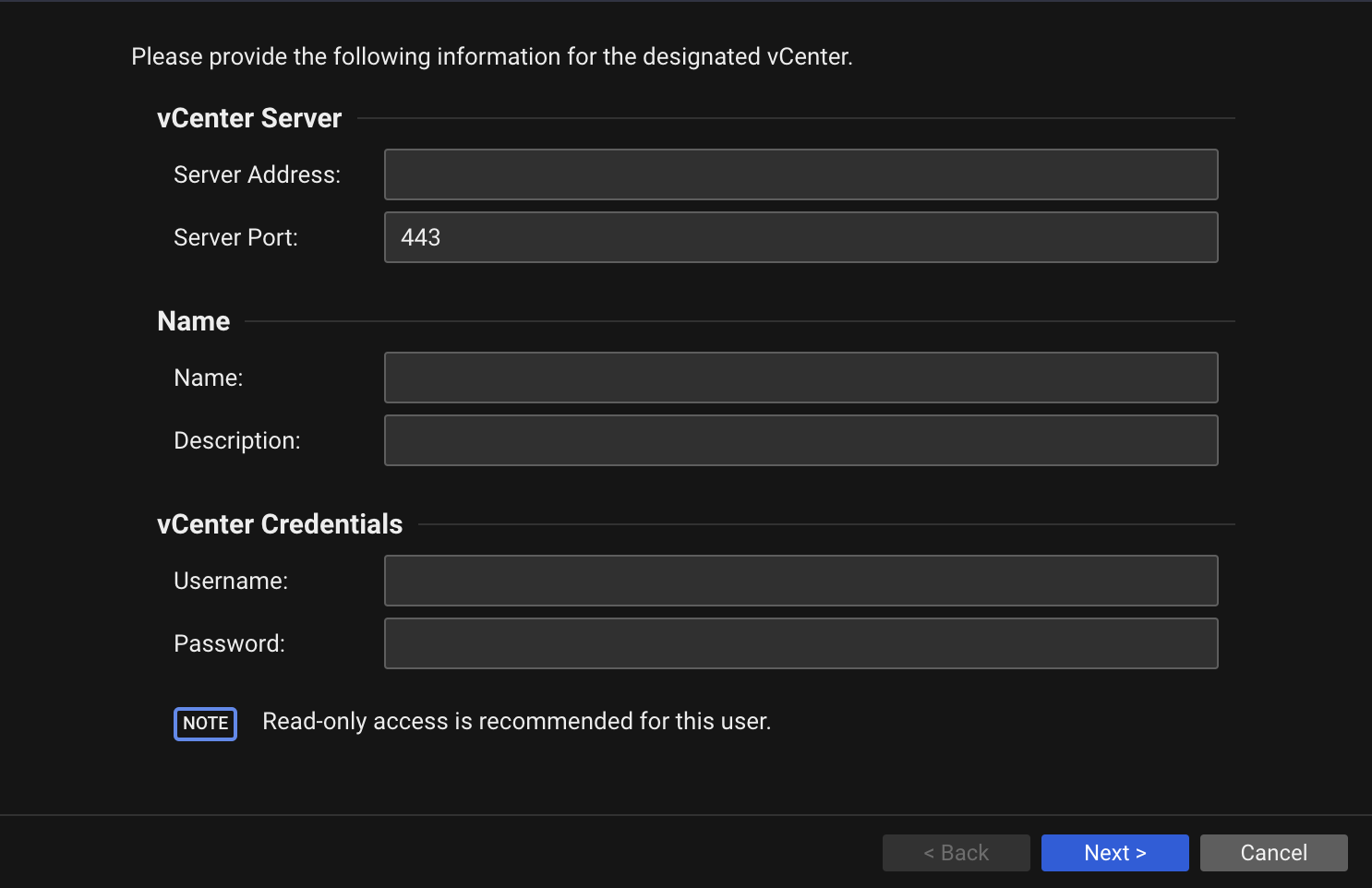
|
|---|
VMware vCenter Synchronization
| Description | Server & Workload Protection periodically synchronizes the virtual machine metadata from VMware vCenter via the Data Center Gateway. During this process the Data Center Gateway collects the following information for general product operation as well as analytics. |
|---|
| Data Collected | - For Data Center Gateways
- For vCenter servers
- vCenter UUID (Moref)
- vCenter version
- vCenter build
- Custom fields
- For virtual machines
- Name
- Parent
- Hardware devices
- vApp Configs
- vmtool status
- IP address
- Network config
- Hostname
- Parent vApp
- Resource pool
- Runtime power state
- Runtime boot time
- Runtime suspend time
- Annotation
- Instance uuid
- Memory size in mb
- Number of cpu
- UUID
- Custom value
- For host systems (ESXI)
- Name
- Parent
- Network configuration
- Kernel module system
- Kernel module patch
- Hardware
- Summary
- Custom value
- For DataCenter
- Name
- Parent
- hostFolder
- vmFolder
- For vApp Folder
- For Compute Resource, Folder, Resource pool, Data store
|
|---|
| Console Location | IP Address of the Data Center Gateway will not be displayed in the console or any customer facing location For the rest, will be shown in Computers page. |
|---|
| Console Settings | 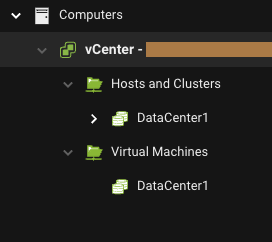
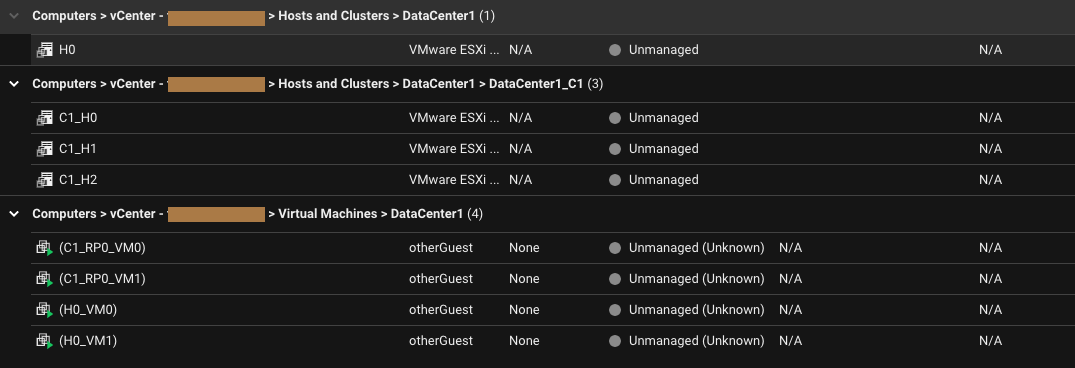
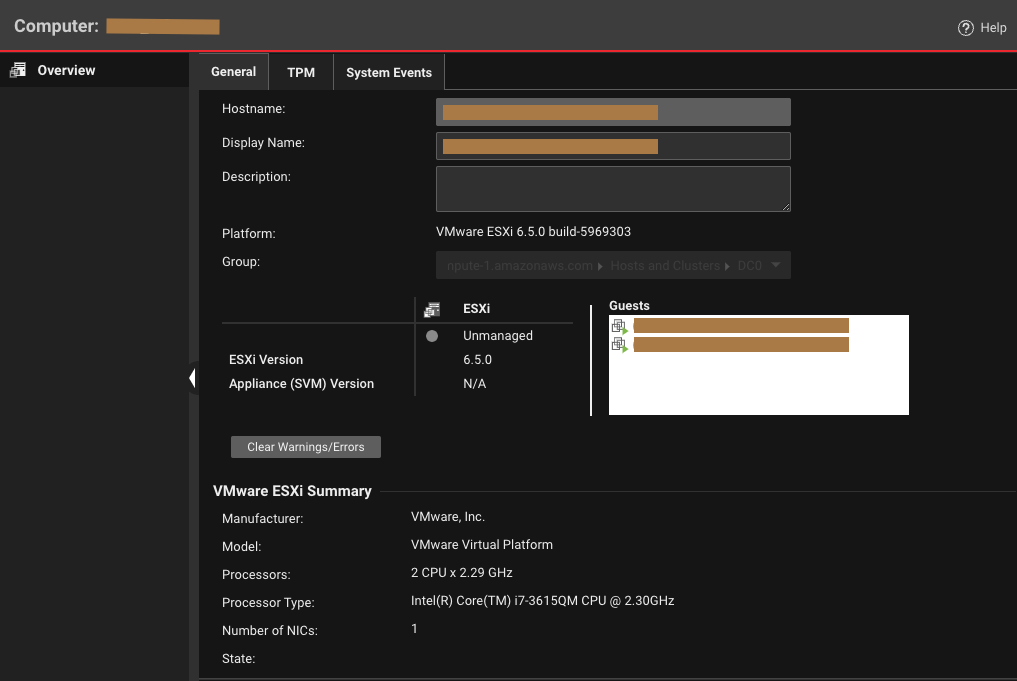
|
|---|
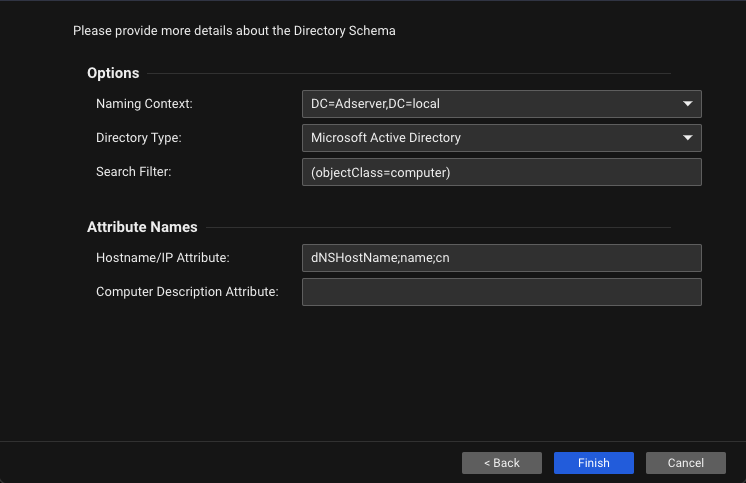
Active Directory Registration
| Description | Add an Active Directory connector in Server & Workload Protection to synchronize computer data from the domain. The data collected is encrypted and stored. |
|---|
| Data Collected | - Active Directory Server Address
- Active Directory Server Port
- The username and password of a domain user which used to fetch data from Active Directory Server
|
|---|
| Console Location | Computers > Add |
|---|
| Console Settings | 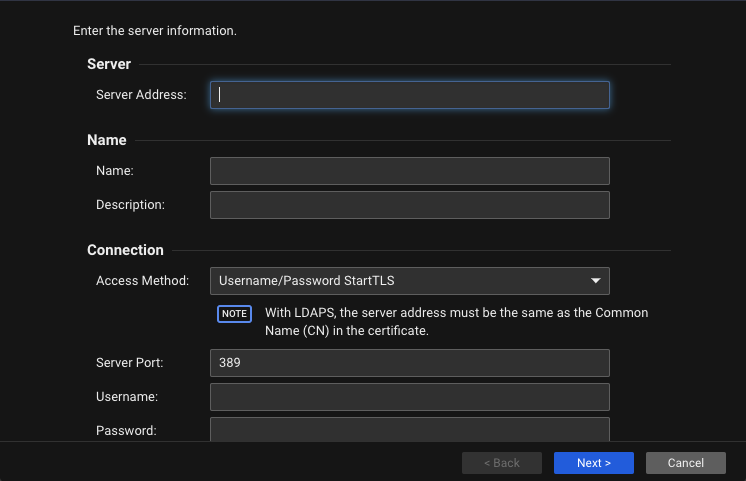
|
|---|
Active Directory Synchronization
| Description | Server & Workload Protection periodically synchronizes the computers' metadata from Active Directory via the Data Center Gateway. During this process, the Data Center Gateway collects the following information for general product operation and analytics. |
|---|
| Data Collected | - For Data Center Gateways
- For Domain Controller
- For Computers
- Name
- DistinguishedName
- Hardware devices
- IP address
- Network config
- Hostname
- Runtime power state
- Runtime boot time
- Runtime suspend time
- BIOS UUID
- Object GUID
|
|---|
| Console Location | The IP address of the Data Center Gateway will not be displayed in the console, or in any customer facing location. The rest of the collected data will be viewable from the Computers page. |
|---|
| Console Settings | 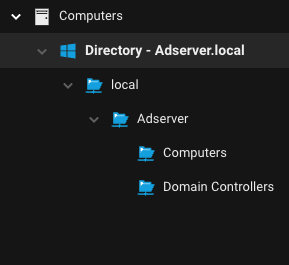
|
|---|
Anti-Malware Module: Agent Metrics Collection and Analytics Service
| Description | The Agent metrics are collected to understand how the agent is performing in a particular environment.
Based on the "Top N" data described below, Trend Micro can provide a suitable exclusion lists to mitigate possible performance issues. |
|---|
| Data Collected | - Top N Scanned Files - File paths that are scanned the most
|
|---|
| Console Location | This is automatically collected via agent metrics and cannot be disabled. |
|---|
Network Module: Agent Metrics Collection and Analytics Service
| Description | The Agent metrics are collected to understand how the agent is performing in a particular environment.
Based on the data collection below, Trend Micro can provide better Intrusion Prevention and Firewall support for the most popular connection invokers. |
|---|
| Data Collected | - Process Command Line - command line that process used to set up the connection
- Process Executable Path - file path of the process that set up the connection
- Process Name - file name of the process that set up this connection
|
|---|
| Console Location | This is automatically collected via agent metrics and cannot be disabled. |
|---|
Smart Feedback
| Description | Smart Feedback enables you to participate, share, and leverage Trend Micro’s global database of threat-related intelligence to rapidly identify and defend against potential threats within your unique network environment.
Smart Feedback is enabled by default for new customers. |
|---|
| Data Collected | - Host name
- IP address
- File name
- File path
- Suspicious file content
- Industry
- Country
|
|---|
| Console Location | Administration > System Settings > Smart Feedback |
|---|
| Console Settings | To disable Trend Micro Smart Feedback, uncheck the Enable Trend Micro Smart Feedback checkbox. 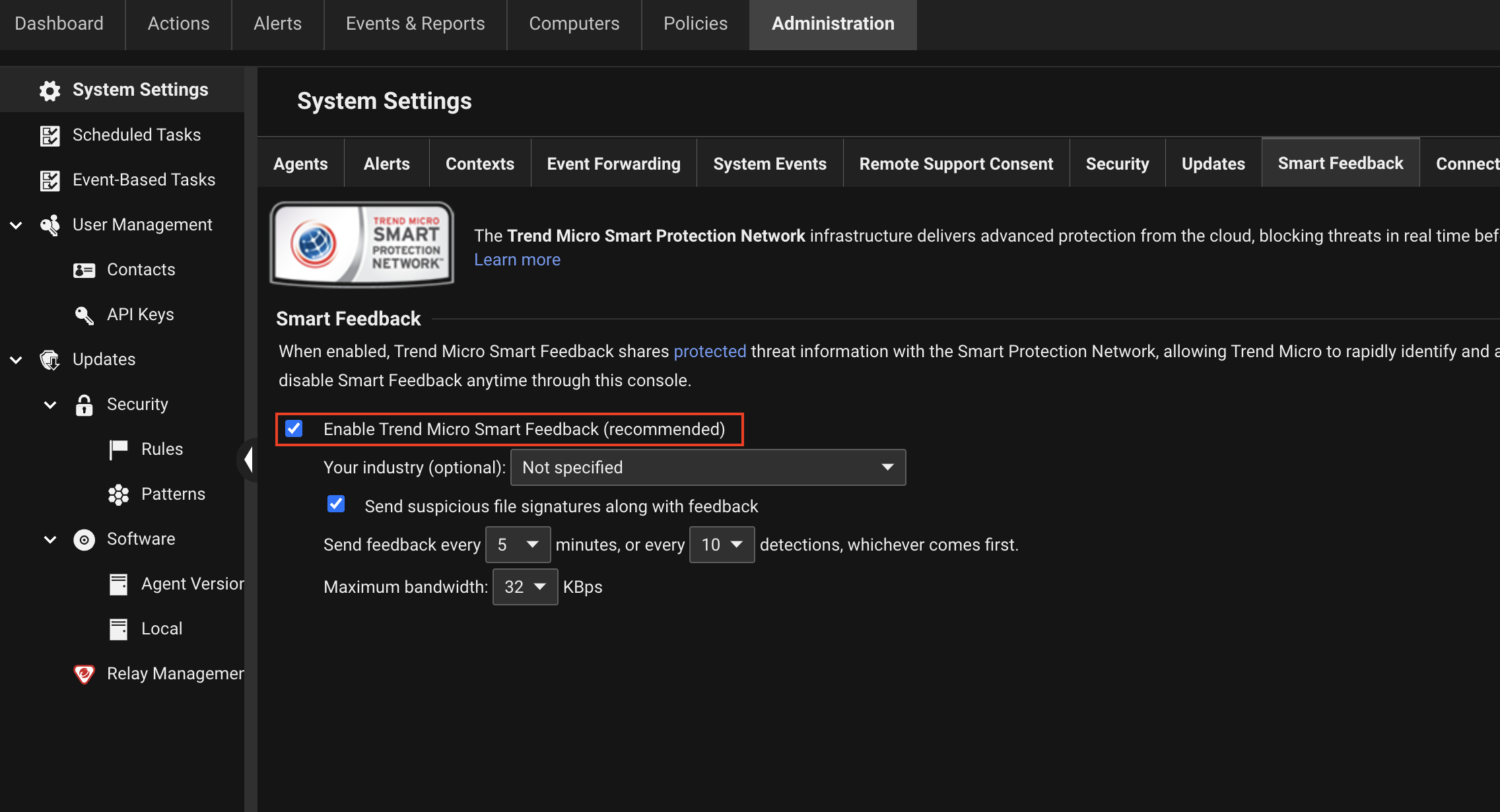
|
|---|


