Summary
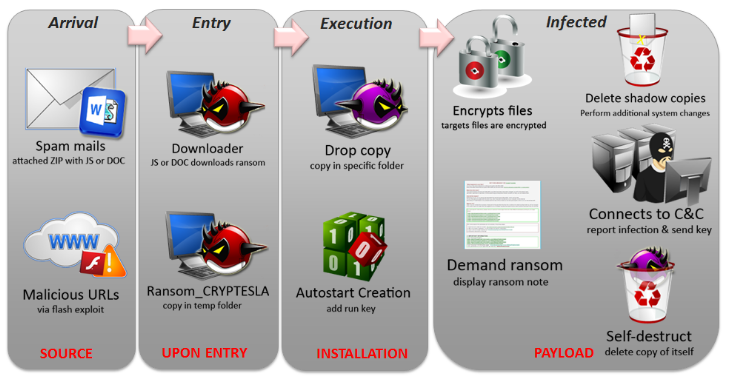
TESLACRYPT, detected as Ransom_CRYPTESLA, which appeared at the start of 2015, was initially a clone of CryptoLocker (Ransom_CRILOCK) as seen in its ransomware message while employing "elliptic curve cryptography" for its encryption. It then moved on to use CryptoWall’s (Ransom_CRYPWALL) template.
A unique feature of this ransomware is its support for encrypting gaming-related files. A few examples are games like Minecraft, Starcraft II, and World of Warcraft.
Initially, TeslaCrypt left important files (key.dat, storage.bin) in the user’s machine that may enable the user to decrypt the ransomware-encrypted files. In December 2015, a decryption utility was made public, allowing users to recover their files by generating the decryption key from an encrypted file. This was true for TeslaCrypt 2.2.0 and below. However, a new version (3.0.0) surfaced in January 2016 which fixed this workaround.
Currently, TeslaCrypt 3.0.0 appends the following extensions to the encrypted files: *.xxx, *.ttt, *.micro, *.mp3.
Antispam Pattern
| LAYER | DETECTION | PATTERN VERSION | RELEASE DATE |
| EXPOSURE | Spam mail with JS or DOC attachment | AS 2166 | 3/1/2016 |
VSAPI Pattern (Malicious File Detection)
| LAYER | DETECTION | PATTERN VERSION | RELEASE DATE |
| INFECTION | TROJ_CRYPTESLA.SM | OPR 11.667.00 | 5/13/2016 |
| INFECTION | Ransom_CRYPTESLA.SMC | OPR 12.365.00 | 2/25/2016 |
| INFECTION | Ransom_CRYPTESLA.SMJ6 | OPR 12.363.00 | 2/24/2016 |
| INFECTION | Ransom_CRYPTESLA.SMJ5 | OPR 12.359.00 | 2/22/2016 |
| INFECTION | Ransom_CRYPTESLA.SMA5 | OPR 12.345.00 | 2/15/2016 |
| INFECTION | Ransom_CRYPTESLA.SMJ3 | OPR 12.335.00 | 2/10/2016 |
| INFECTION | Ransom_CRYPTESLA.SMJ4 | OPR 12.335.00 | 2/10/2016 |
| INFECTION | Ransom_CRYPTESLA.SMJ2 | OPR 12.317.00 | 2/5/2016 |
| INFECTION | Ransom_CRYPTESLA.SMA4 | OPR 12.315.00 | 2/3/2016 |
| INFECTION | Ransom_CRYPTESLA.SMKL | OPR 12.311.00 | 2/1/2016 |
| INFECTION | Ransom_HPCRYPTESLA.SM | OPR 12.311.00 | 2/1/2016 |
| INFECTION | Ransom_CRYPTESLA.SMJ1 | OPR 12.305.00 | 1/29/2016 |
| INFECTION | Ransom_CRYPTESLA.SMA2 | OPR 12.287.00 | 1/21/2016 |
| INFECTION | Ransom_HPCRYPTESLA.SMD | OPR 12.281.00 | 1/18/2016 |
| INFECTION | Ransom_CRYPTESLA.SMA3 | OPR 12.255.00 | 1/5/2016 |
| INFECTION | Ransom_CRYPTESLA.SMA1 | OPR 12.253.00 | 1/4/2016 |
| INFECTION | Ransom_CRYPTESLA.SMA0 | OPR 12.241.00 | 12/29/2015 |
| INFECTION | Ransom_CRYPTESLA.SMB | OPR 12.231.00 | 12/24/2015 |
| INFECTION | Ransom_CRYPTESLA.SMA | OPR 12.229.00 | 12/23/2015 |
| INFECTION | Ransom_CRYPTESLA.SM1 | OPR 12.213.00 | 12/15/2015 |
| INFECTION | Ransom_CRYPTESLA.SM0 | OPR 12.205.00 | 12/11/2015 |
| INFECTION | Ransom_CRYPTESLA.SMM | OPR 12.199.00 | 12/8/2015 |
| INFECTION | Ransom_CRYPTESLA.SM | OPR 12.189.00 | 12/3/2015 |
| INFECTION | TROJ_CRYPTESLA.SMB | OPR 11.693.00 | 5/26/2015 |
| INFECTION | TROJ_CRYPTESLA.SM3 | OPR 11.691.00 | 5/25/2015 |
| INFECTION | TROJ_CRYPTESLA.SMA | OPR 11.683.00 | 5/21/2015 |
| INFECTION | TROJ_CRYPTESLA.SM2 | OPR 11.671.00 | 5/15/2015 |
| INFECTION | TROJ_CRYPTESLA.SM1 | OPR 11.665.00 | 5/12/2015 |
WRS Pattern (Malicious URL and Classification)
| LAYER | URL | CATEGORY | BLOCKING DATE |
| CLEAN-UP | dawnlogistics{blocked}.com/wp-cont/themes/sketch/dbsys.php | Disease Vector | 1/13/2016 |
| CLEAN-UP | yavuzturk{blocked}.com/wp-includes/dbsys.php | Disease Vector | 1/13/2016 |
| CLEAN-UP | elle-ectric{blocked}.com/wp-cont/themes/sketch/dbsys.php | Disease Vector | 1/13/2016 |
| CLEAN-UP | f1autobody{blocked}.com/wp-cont/themes/sketch/dbsys.php | Disease Vector | 1/13/2016 |
| CLEAN-UP | nicasitios{blocked}.com/dbsys.php | Disease Vector | 1/13/2016 |
| CLEAN-UP | tactiva{blocked}.org/installation1/view/database/dbconnect.php | Disease Vector | 2/3/2016 |
| CLEAN-UP | westhollywooddaloffice{blocked}.com/dbconnect.php | Disease Vector | 2/3/2016 |
| CLEAN-UP | {blocked}198.1.95.93/~deveconomytravel/cache/binstr.php | Disease Vector | 4/7/2016 |
| CLEAN-UP | kel52{blocked}.com/wp-cont/plugins/ajax-admin/binstr.php | Disease Vector | 3/15/2016 |
| INFECTION | 46.151.52.231/87{blocked}.exe?1 | Disease Vector | 3/2/2016 |
| INFECTION | firstwetakemanhat{blocked}.com/91.exe?1 | Disease Vector | 12/30/2015 |
| INFECTION | 46.151.52.196/86{blocked}.exe?1 | Disease Vector | 12/25/2015 |
| INFECTION | 46.151.52.197/85{blocked}.exe?1 | Disease Vector | 3/2/2016 |
| INFECTION | 91.224.161.116 /clv002/f32{blocked}.bin | Disease Vector | 2/5/2016 |
| INFECTION | arendroukysdqq{blocked}.com/25.exe | Disease Vector | 3/2/2016 |
| INFECTION | arendroukysdqq{blocked}.com/80.exe | Disease Vector | 3/2/2016 |
| INFECTION | arendroukysdqq{blocked}.com/85.exe | Disease Vector | 3/2/2016 |
| INFECTION | arendroukysdqq{blocked}.com/90.exe | Disease Vector | 3/2/2016 |
| INFECTION | artskorat{blocked}.com/html/images/69.exe | Disease Vector | 3/2/2016 |
| INFECTION | belablebil{blocked}.com/51.exe?1 | Disease Vector | 2/15/2016 |
| INFECTION | belablebi{blocked}l.com/80.exe?1 | Disease Vector | 2/13/2016 |
| INFECTION | belableqq{blocked}. com/80.exe?1 | Disease Vector | 3/2/2016 |
| INFECTION | belableqq{blocked}.com/51.exe?1 | Disease Vector | 2/15/2016 |
| INFECTION | belableqq{blocked}.com/80.exe?1 | Disease Vector | 3/2/2016 |
| INFECTION | fernytowd{blocked}. com/69.exe?1 | Disease Vector | 3/2/2016 |
| INFECTION | fernytowd{blocked}. com/90.exe?1 | Disease Vector | 3/2/2016 |
| INFECTION | fernytowd{blocked}.com/69.exe?1 | Disease Vector | 3/2/2016 |
| INFECTION | fernytowd{blocked}.com/69.exe?1 | Disease Vector | 3/2/2016 |
| INFECTION | fernytowd{blocked}.com/69.exe?1 | Disease Vector | 3/2/2016 |
AEGIS Pattern (Behavior Monitoring Pattern)
| LAYER | DETECTION | PATTERN VERSION | RELEASE DATE |
| CLEAN-UP | 1922F | OPR 1523 | 3/15/2016 |
| CLEAN-UP | 1970T | OPR 1533 | 04/12/16 |
| CLEAN-UP | 1970F | OPR 1527 | 3/29/2016 |
| CLEAN-UP | 1971T | OPR 1533 | 04/12/16 |
| CLEAN-UP | 1971F | OPR 1527 | 3/29/2016 |
| CLEAN-UP | 1972T | OPR 1533 | 04/12/16 |
| CLEAN-UP | 1972F | OPR 1527 | 3/29/2016 |
| CLEAN-UP | 1973T | OPR 1533 | 4/12/2016 |
| CLEAN-UP | 1973F | OPR 1529 | 4/5/2016 |
| CLEAN-UP | 1977F | OPR 1535 | 4/19/2016 |
| CLEAN-UP | 1977T | OPR 1537 | 4/26/2016 |
DCT Pattern (System Clean Pattern)
| LAYER | DETECTION | PATTERN VERSION | RELEASE DATE |
| CLEAN-UP | TSC_GENCLEAN | LATEST DCT OPR | BUILT-IN |
Network Pattern
| LAYER | DETECTION | PATTERN VERSION | RELEASE DATE |
| CLEAN-UP | HTTP_RANSOM_CRYPTESLA_RESPONSE | RR 1.10139.00 | 1/5/2016 |
| CLEAN-UP | HTTP_RANSOM_CRYPTESLA_REQUEST-4 | RR 1.10151.00 | 3/15/2016 |
| CLEAN-UP | HTTP_RANSOM_CRYPTESLA_REQUEST-5 | RR 1.10151.00 | 3/15/2016 |
Make sure to always use the latest available pattern to detect old and new variants of Ransom_CRYPTESLA.
Solution Map
| Major Products | Versions | Virus Pattern | Behavior Monitoring | Web Reputation | DCT Pattern | Antispam Pattern | Network Pattern |
|---|
OfficeScan |
10.6 and above |
Update Pattern via web console |
Update Pattern via web console |
Enable Web Reputation Service* |
Update Pattern via web console |
N/A | Update Pattern via web console |
|---|
Worry-Free Business Suite | Standard |
N/A |
|---|
Advanced/MSA | Update Pattern via web console |
|---|
| Services | N/A |
|---|
| Hosted Email Security |
N/A |
N/A | Update Pattern via web console |
|---|
| Deep Security |
8.0 and above | Update Pattern via web console |
N/A | Update Pattern via web console |
|---|
ScanMail | SMEX 10 and later |
N/A |
Update Pattern via web console |
N/A |
|---|
| SMD 5 and later |
|---|
| InterScan Messaging | IMSVA 8.0 and above |
|---|
| InterScan Web | IWSVA 6.0 and later |
|---|
| Deep Discovery | DDI 3.0 and later |
N/A | Update Pattern via web console |
|---|
*Refer to the Product Administrator’s Guide on how to enable the Email Reputation or Web Reputation services features.
Recommendations
Threat Report
Blog
Additional Remarks
- For OfficeScan
There have been reports of a CRYPTESLA variant running under UNC path. A hot fix has been released to detect this kind of behavior. Please contact Trend Micro Technical Support to request for OfficeScan 11.0 SP1 Hotfix Build 4828.
- For Worry-Free Business Suite (WFBS)
Please ensure that WFBS is updated with the latest service pack release, WFBS 9 SP3. You may download it here.


