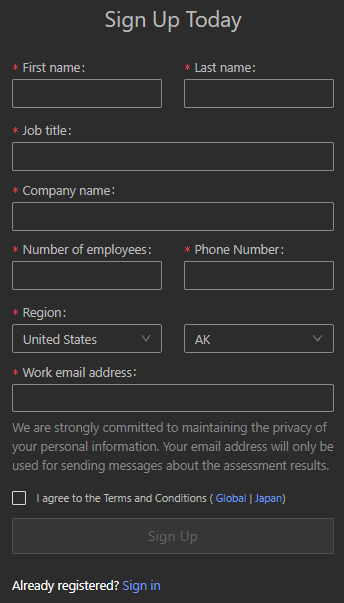
Registration
The service uses the information to:
- Identify users
- Assign an ID to the company (The ID is embedded in the Endpoint Assessment Tool package.)
- Send status updates
- Generate email and endpoint reports
| Data collected |
- First name
- Last name
- Email address
- Phone number
- Company
- Number of employees
- Job title
- Country
|
|---|
| Console location |
Registration page
|
|---|
| Console settings |
|
|---|
Back to top
Email Assessment (Office 365)
The service needs permission to access mailboxes for scanning. Trend Micro does not access and store users’ Office 365 credentials.
Email Assessment combines machine learning, document exploit detection, and behavior analysis to protect Exchange Online users from BEC, ransomware, advanced phishing, and other high-profile attacks.
| Data collected |
- Azure Active Directory: Domain, user, and group information
- Exchange Online: Mailbox information
- Global administrator email address used to grant permissions to the Assessment Service
- Email senders
- Email recipients
- Email locations
- Email subjects
- Email attachments
- File modifiers
- File locations
- File names
- URLs in email body
- URLs in email attachments
- URLs in files
- Suspicious executable files and scripts in cloud storage services
- Suspicious executable files and scripts in email attachments
- Metadata of suspicious executable files and scripts in cloud storage services
- Metadata of suspicious executable files and scripts in email attachments
- IP addresses of upstream MTAs for IP rating query
- Domain, user, device and group information in Azure Active Directory
|
|---|
| Console location |
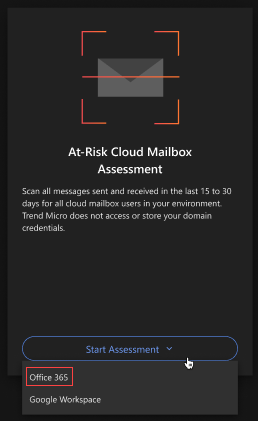
At-Risk Cloud Mailbox Assessment
|
|---|
| Console settings |
- Click Start Assessment.
- Select Office 365.
|
|---|
Back to top
Email Assessment (Google Workspace)
The service needs permission to access mailboxes for scanning. Trend Micro does not access and store users’ Google Workspace credentials.
Email Assessment combines machine learning, document exploit detection, and behavior analysis to protect Exchange Online users from BEC, ransomware, advanced phishing, and other high-profile attacks.
| Data collected |
- Domain, user, and group information
- Global administrator email address for Gmail
- Email senders
- Email recipients
- Email locations
- Email subjects
- Email attachments
- File modifiers
- File locations
- File names
- URLs in email body
- URLs in email attachments
- URLs in files
- Suspicious executable files and scripts in cloud storage services
- Suspicious executable files and scripts in email attachments
- Metadata of suspicious executable files and scripts in cloud storage services
- Metadata of suspicious executable files and scripts in email attachments
- IP addresses of upstream MTAs for IP rating query
- Domain, user, device and group information in Azure Active Directory
|
|---|
| Console location |
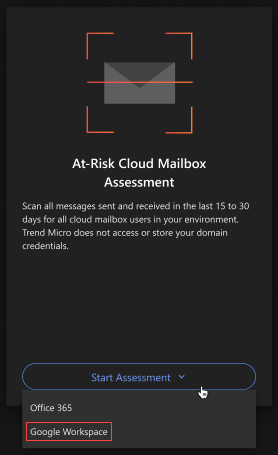
At-Risk Cloud Mailbox Assessment
|
|---|
| Console settings |
- Click Start Assessment.
- Select Google Workspace.
|
|---|
Back to top
Endpoint Assessment (Windows)
The assessment tool scans Windows endpoints for malicious files, critical vulnerabilities, and threat indicators collected from global intelligence sources. After collecting system information, the tool automatically uploads the data to the service for in-depth analysis and reporting.
| Data collected |
- Host name
- Endpoint name
- IP address
- MAC address
- File name
- File path
- Unpatched critical vulnerabilities
|
|---|
| Console location |
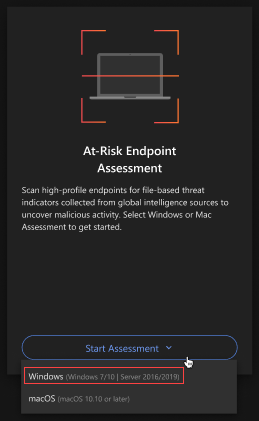
At-Risk Endpoint Assessment
|
|---|
| Console settings |
Click Start Assessment.
Select Windows.
|
|---|
Back to top
Endpoint Assessment (macOS)
The assessment tool scans macOS endpoints for file-based threat, network detection and operation system possible security risks. After collecting system information, the tool automatically uploads the data to the service for in-depth analysis and reporting.
| Data collected |
- Installed Apps primary executable attributes: file path, file hash, create time, owner use name, file mode, code sign status
- Active process's image file attributes: file path, file hash, create time, owner use name, file mode, code sign status
- All persistent items files attributes: file path, file hash, create time, owner use name, file mode, code sign status
- Installed applications, active processes, and persistent processes:
- File path
- File hash value
- Time created
- User name of owner
- File permission
- Code signing status
- All suspicious network connections basic information:
- Source IP address/port
- Destination IP address/port
- Relating process information
- Suspicious connections:
- Source IP address and port
- Destination IP address and port
- Related process information
- Operating system:
- Version
- macOS user account
- Status of key security features
|
|---|
| Console location |
At-Risk Endpoint Assessment
|
|---|
| Console settings |
- Click Start Assessment.
- Select macOS.
|
|---|
Back to top
Trend Micro Vision One Risk Assessment
Zero Trust Risk Insights allows you to quickly assess the cloud access activities and vulnerabilities related to users and devices, and to determine how to mitigate the risks found in your network.
Back to top


