- Phishing and other suspicious content
 Back to top Back to top
Graymail
Trend Micro Email Security uses Trend Micro Antispam Engine to protect users from graymail.
Disabling the criteria prevents the mentioned data from being sent to Trend Micro, but severely affects the ability of Trend Micro Email Security to detect graymail.
| Data transmitted to Trend Micro |
- Mail Header "From"/"To"
- Mail Message-ID
- Mail Subject
- Mail Reply-To
- Mail Return-Path
- Mail SHA1
- URL and its properties
- Envelope From/RCPT/HELO
- Attachment SHA1
- Date in the Header
- Routing information in Received field
|
|---|
| Feature Configuration Location | Inbound Protection > Spam Filtering > Spam Policy > Policy Name > Scanning Criteria |
|---|
| Console settings |
Click the image to enlarge.
|
|---|
Back to top
Social Engineering Attack
Trend Micro Email Security uses Trend Micro Antispam Engine to protect users from social engineering attacks.
Disabling the criteria prevents the mentioned data from being sent to Trend Micro, but severely affects the ability of Trend Micro Email Security to detect social engineering attacks.
| Data transmitted to Trend Micro |
- Mail Header "From"/"To"
- Mail Message-ID
- Mail Subject
- Mail Reply-To
- Mail Return-Path
- Mail SHA1
- URL and its properties
- Envelope From/RCPT/HELO
- Attachment SHA1
- Date in the Header
- Routing information in Received field
|
|---|
| Feature Configuration Location | Inbound Protection > Spam Filtering > Spam Policy > Policy Name > Scanning Criteria |
|---|
| Console settings |
- Social engineering attack
Click the image to enlarge.
|
|---|
Back to top
High Profile Users
Trend Micro Email Security allows administrators to add high profile users that may be frequently forged or spoofed, either by manually adding single users or by synchronizing groups from directories.
If a high profile user is deleted, Trend Micro Email Security does not check incoming email messages from this user for BEC attacks any more.
| Data transmitted to Trend Micro |
- First names
- Middle names
- Last names
- Group names
- Email addresses
|
|---|
| Feature Configuration Location | Inbound Protection > Spam Filtering > Business Email Compromise (BEC) |
|---|
| Console settings |
|
|---|
Back to top
Web Reputation
Trend Micro Email Security leverages Trend Micro Web Reputation Services to scan URLs contained in email subject, body and attachments to detect malicious URLs based on their reputation scores.
Disabling Web Reputation prevents the mentioned data from being sent to Trend Micro, but severely affects the ability of Trend Micro Email Security to detect malicious URLs.
| Data transmitted to Trend Micro |
- URLs in email body
- URLs in email subjects
- URLs in attachments
|
|---|
| Feature Configuration Location | Inbound Protection > Spam Filtering > Spam Policy > Policy Name > Scanning Criteria |
|---|
| Console settings |
Click the image to enlarge.
|
|---|
Back to top
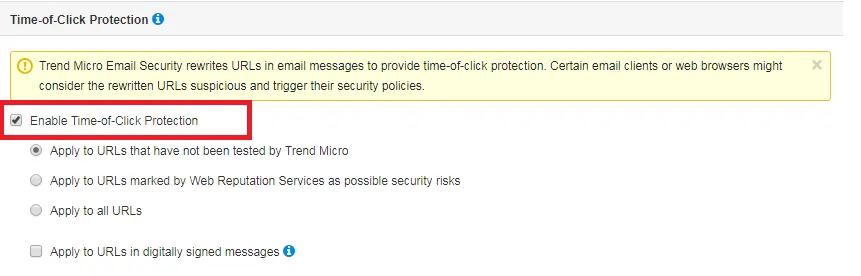
Time-of-Click Protection
Trend Micro Email Security leverages Trend Micro’s Time-of-Click Protection service to provide the ability to rewrite URLs in the email message body during scanning, and analyze the URLs at the time when the message recipient clicks on these URLs.
Disabling Time-of-Click Protection prevents the mentioned data from being sent to Trend Micro, but severely affects the ability of Trend Micro Email Security to detect malicious URLs.
| Data transmitted to Trend Micro |
|
|---|
| Console location | Inbound Protection > Spam Filtering > Spam Policy > Policy Name > Scanning Criteria > Web Reputation |
|---|
| Feature Configuration Location |
- Enable Time-of-Click Protection
Click the image to enlarge.
|
|---|
Back to top
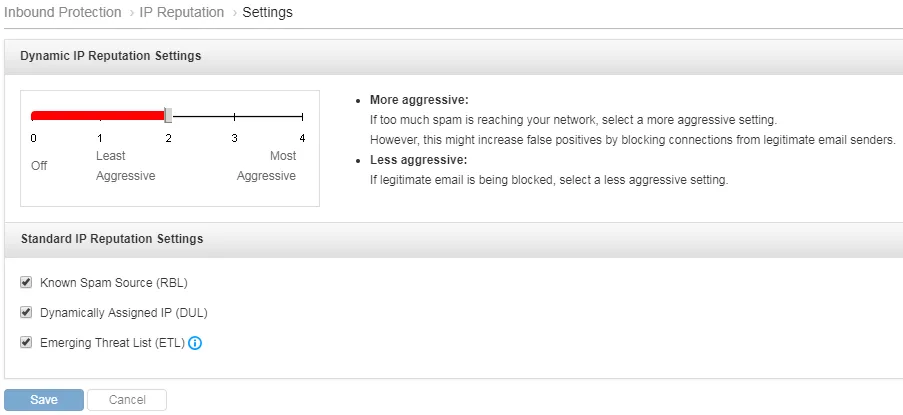
IP Reputation
Trend Micro Email Security leverages Trend Micro Email Reputation Services to verify IP addresses of incoming email messages using one of the world's largest, most trusted reputation database, along with a dynamic reputation database to identify new spam and phishing sources, stopping even zombies and botnets as they first emerge.
Disabling IP Reputation prevents the mentioned data from being sent to Trend Micro, but severely affects the ability of Trend Micro Email Security to detect and block spam from known and emerging spam sources.
| Data transmitted to Trend Micro |
- Source IP addresses of incoming email messages
|
|---|
| Feature Configuration Location | Inbound Protection > Connection Filtering > IP Reputation > Settings
Click the image to enlarge.
|
|---|
Back to top
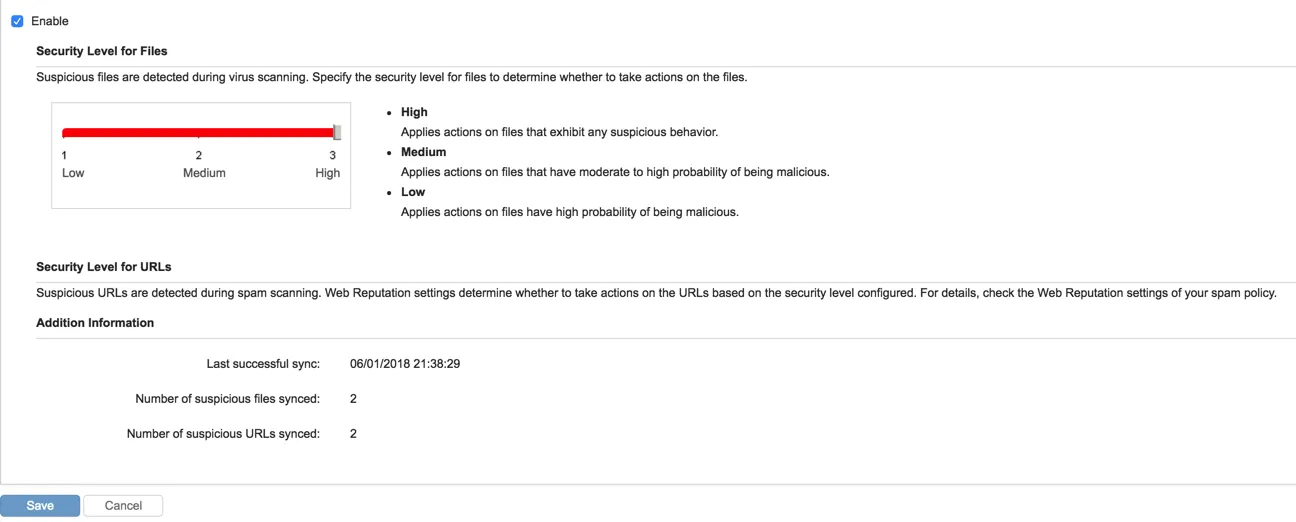
Suspicious Objects
After Trend Micro Email Security is registered to Trend Micro Control Manager, Control Manager automatically synchronizes the suspicious objects with Trend Micro Email Security at a scheduled time interval. In addition to its own scanning mechanism, Trend Micro Email Security implements these suspicious objects during URL and file scanning.
Customers can make configurations on the Control Manager to stop synchronizing suspicious objects.
The mentioned data will be purged after the administrator account is deprovisioned.
| Data transmitted to Trend Micro |
|
|---|
| Feature Configuration Location | Administration > Suspicious Objects
Click the image to enlarge.
|
|---|
Back to top
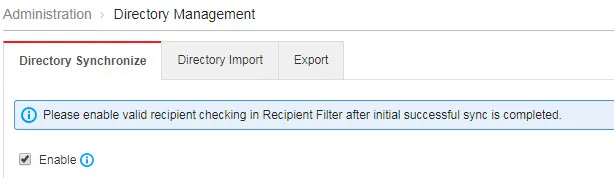
Directory Synchronization
Trend Micro Email Security provides a synchronization tool that enables you to synchronize your current groups and email accounts from Open LDAP, Microsoft Active Directory, Microsoft AD Global Catalog, Microsoft Office 365/Microsoft Entra ID and IBM Domino servers to the Trend Micro Email Security server.
The mentioned data will be purged after the administrator account is deprovisioned.
| Data transmitted to Trend Micro |
- Display names
- Email addresses
- Group email addresses
- Group and member relationships
- Email aliases
- LDAP information (host name, port, base DN/tenant domain, Use SSL)
|
|---|
| Feature Configuration Location | Administration > Directory Management > Directory Synchronize
Click the image to enlarge.
|
|---|
Back to top
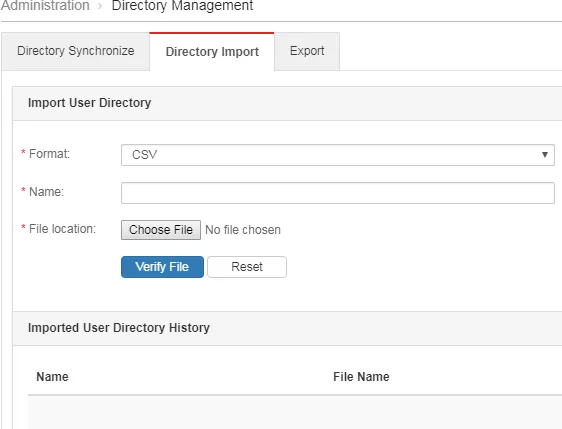
Directory Import
Directory Import allows administrators to import a list of valid recipients’ email addresses and display names from a CSV file.
The mentioned data will be purged after the administrator account is deprovisioned.
| Data transmitted to Trend Micro |
- Display names
- Email addresses
|
|---|
| Feature Configuration Location | Administration > Directory Management > Directory Import
Click the image to enlarge.
|
|---|
Back to top
Logs
Trend Micro Email Security stores logs of all processed email messages for the administrator to use and query. Policy event logs and URL click tracking logs are kept for 30 days, and mail tracking logs are kept for 90 days.
Audit logs are kept for 12 months, but the administrator can query audit logs of up to 30 days. The number of days kept is not configurable.
After scheduled log deletion, all log data will be purged and cannot be retrieved.
| Data transmitted to Trend Micro |
- Sender email addresses
- Recipient email addresses
- Email subjects
- Sender IP addresses
- Recipient IP addresses
- Attachment names and hash
- Message IDs
|
|---|
| Feature Configuration Location | Logs
Click the image to enlarge.
|
|---|
Back to top
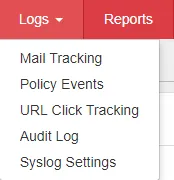
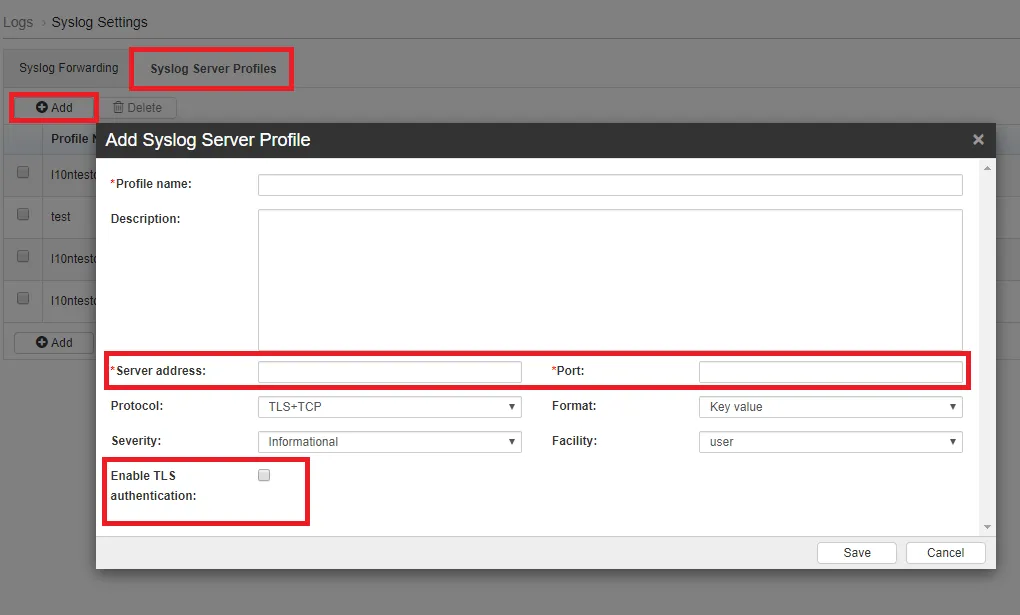
Syslog
Trend Micro Email Security allows you to forward syslog messages to an external syslog server in a structured format, which allows third-party application integration.
The mentioned data will be purged after the syslog server profiles are deleted or the administrator account is deprovisioned.
| Data transmitted to Trend Micro |
- Syslog server addresses, ports and protocols
- Certificates for TLS authentication
|
|---|
| Feature Configuration Location | Logs > Syslog Settings > Syslog Server Profiles
Click the image to enlarge.
|
|---|
Back to top
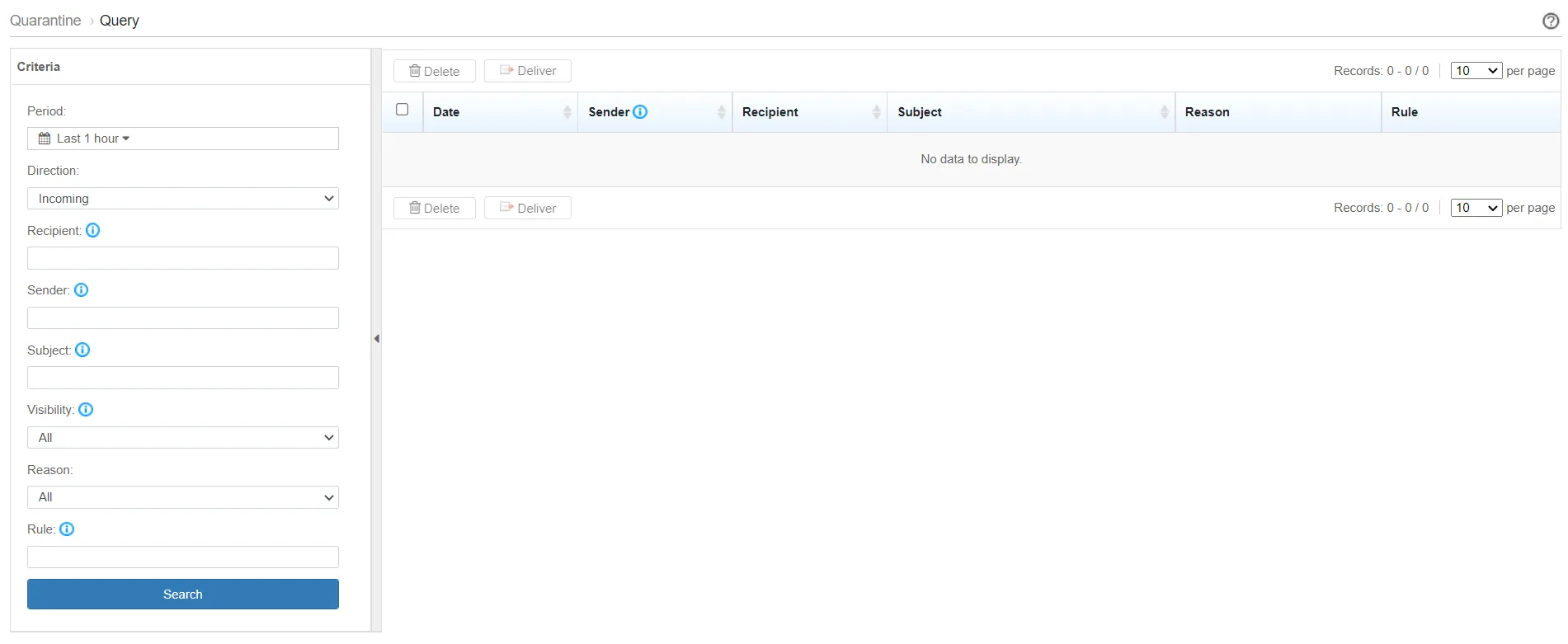
Quarantine
Email messages quarantined for any reason are kept by Trend Micro Email Security for a maximum of 30 days. During this period, the administrator may be able release them or inspect them if further analysis is required. After that period, the data will be purged permanently.
| Data transmitted to Trend Micro |
- Email messages quarantined
|
|---|
| Feature Configuration Location | Quarantine > Query
Click the image to enlarge.
|
|---|
Back to top
Email Continuity
Trend Micro Email Security provides protection against email loss if your email server goes down. If your server becomes unavailable due to a crash or network connectivity problem, Trend Micro Email Security automatically transfers inbound traffic to a backup server until your server is back online.
Disabling this feature will prevent end users from using the continuity mailbox provided on the End User Console to manage their email messages when the email server goes down.
The mentioned data will be purged after the administrator account is deprovisioned.
| Data transmitted to Trend Micro |
- Email data and metadata (including subjects and sender addresses)
|
|---|
| Feature Configuration Location | Administration > Email Continuity
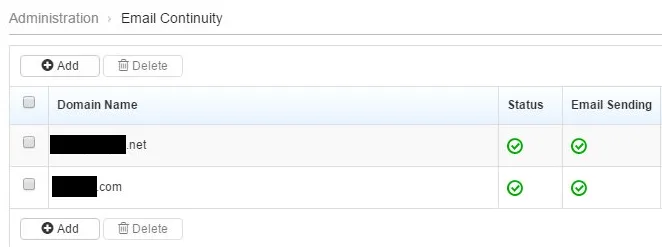
Click the image to enlarge.
|
|---|
Back to top
Single Sign-On
If single sign-on (SSO) is enabled and required settings are completed in Administrator Management, Trend Micro Email Security allows subaccounts to access the administrator console with their existing identity provider credentials.
If SSO is enabled and required settings are completed in End User Management, Trend Micro Email Security allows end users to access the administrator console with their existing identity provider credentials.
| Data transmitted to Trend Micro |
- Logon URLs
- Logoff URLs
- Claim type
- Certificate file downloaded from the identity provider
|
|---|
| Feature Configuration Location |
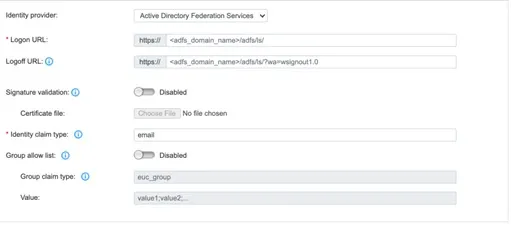
Click the image to enlarge.
|
|---|
Back to top
Address Groups
Trend Micro Email Security allows administrator to configure email addresses in an address group.
And the groups can be configured in policy’s Recipients and Senders.
The mentioned data will be purged after the administrator account is deprovisioned.
| Data transmitted to Trend Micro |
|
|---|
| Feature Configuration Location | Administration > Policy Objects > Address Groups
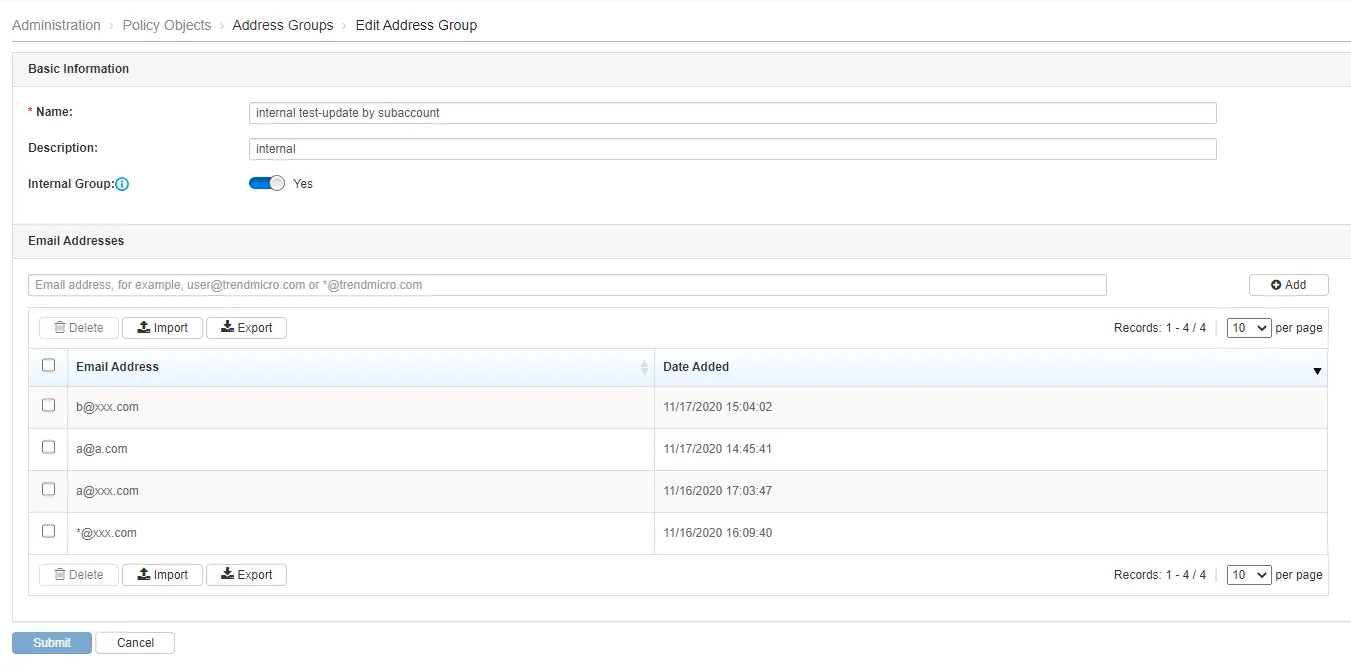
Click the image to enlarge.
|
|---|
Back to top
Logon Access Control
Trend Micro Email Security allows administrators to configure the clients that are allowed to access the administrator console, End User Console, and resources within Trend Micro Email Security by specifying a list of approved IP addresses. Administrators can also optionally specify the email addresses to receive alerts on blocked or logged access.
The mentioned data will be purged after the administrator account is deprovisioned.
| Data transmitted to Trend Micro |
- IP addressses
- Email addresses
|
|---|
| Feature Configuration Location | Administration > Logon Access Control
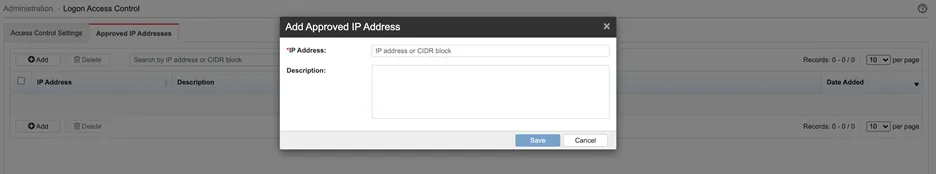
Click the image to enlarge.
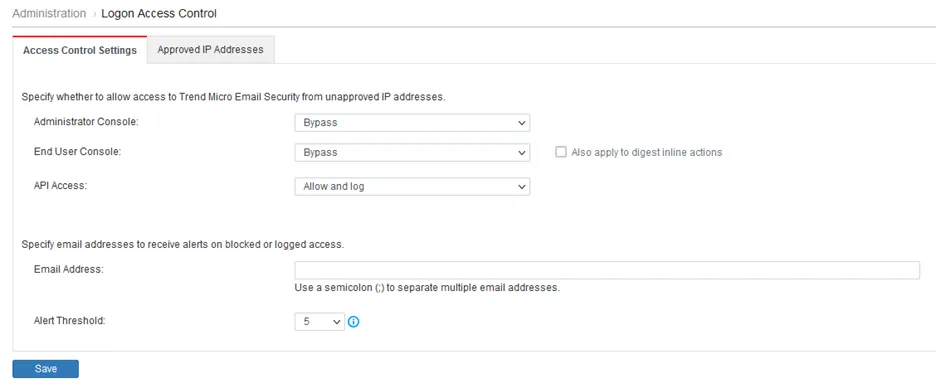
Click the image to enlarge.
|
|---|
Back to top
Managed XDR
Trend Micro Email Security collects metadata and detection logs of email messages, user profiles and managed domains for the intelligent investigation API to discover anomalies for XDR/Managed XDR customers.
All collected metadata and detection logs will be removed after 180 days.
| Data transmitted to Trend Micro | High profile user information, including:
- Display names
- Given names
- Surnames
- Email addresses (if configured)
Managed domain information, including:
- Domain names
- FQDNs or IP addresses of the domains’ inbound SMTP servers
- IP addresses of the domains’ outbound SMTP servers
Detection logs
Email message metadata, including:
- SMTP email addresses
- Email received timestamps
- Email attachment file names
- Email attachment hash values
- True file types of email attachments
- Email attachment sizes
- Email headers
- Email body hash values
- Sender IP addresses
- URLs in email messages
|
|---|
| Feature Configuration Location | Trend Vision One > Point Product Connection > Product Connector
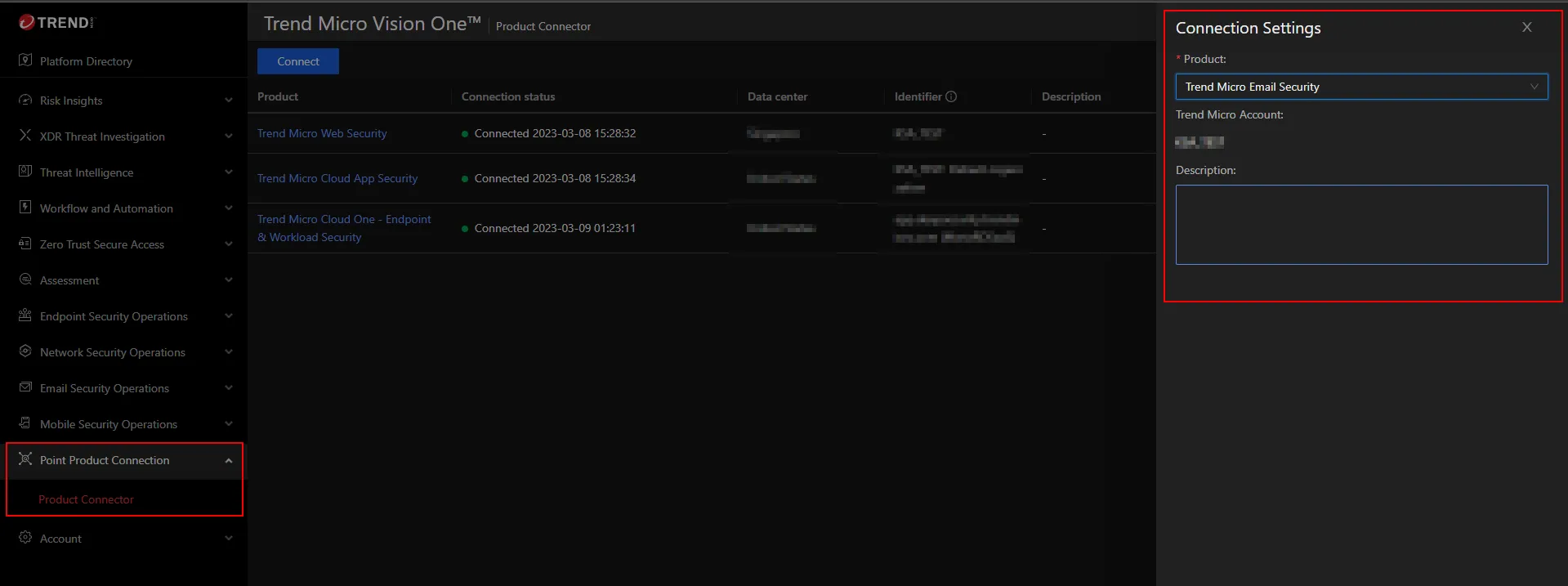
Click the image to enlarge.
|
|---|
Back to top
| 

