Summary
Attention! Attention! Attention!”
“Your documents, photos, databases and other important files have been encrypted!”
Having a “voice” capability to verbally read out a message and inform you that your files are encrypted makes this unique from other ransomware.
This innovative technique is reminiscent of one of the variants of REVETON, otherwise known as police ransomware, that can also “speak” in a language depending on where the user is located or based from.
Based on our investigation, CERBER only uses English language; however, once users click on the link via Tor browser, it points to a page asking users which language to employ. Even though the landing page offers various languages, only English works, as of this posting. The cybercriminals behind CERBER requires users to pay 1.24 BTC (~US$523, as of March 4, 2016), which will increase up to 2.48 BTC (~US$1046, as of March 4, 2016) in seven (7) days’ time.
Based on SPN, this menace is seen mostly in APAC and NABU regions.
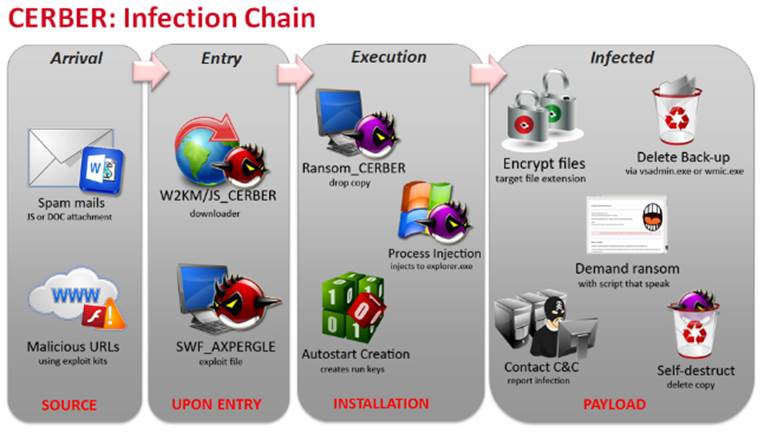
Click image to enlarge.
Antispam Pattern
| LAYER | DETECTION | PATTERN VERSION | RELEASE DATE |
|---|
| EXPOSURE | Spam mail | AS2314 | 5/10/2016 |
SAL / BES Pattern
| LAYER | DETECTION | PATTERN VERSION | RELEASE DATE |
|---|
| INFECTION | SWF.HEU.HeapSpray.A | SAL 121913.0.0 | 5/26/2016 |
VSAPI Pattern (Malicious File Detection)
| LAYER | DETECTION | PATTERN VERSION | Release Date |
|---|
| INFECTION | Ransom_CERBER.SM | 12.497.00 | 4/29/2016 |
| INFECTION | Ransom_CERBER.SMA | 12.497.00 | 4/29/2016 |
| INFECTION | Ransom_CERBER.SMC | 12.497.00 | 4/29/2016 |
| INFECTION | Ransom_CERBER.SMB | 12.502.06 | 5/2/2016 |
| INFECTION | Ransom_CERBER.SMR | 12.504.06 | 5/3/2016 |
| INFECTION | Ransom_CERBER.SMD | 12.524.05 | 5/13/2016 |
| INFECTION | SWF_AXPERGLE.LN | 12.493.00 | 04/27/16 |
WRS Pattern (Malicious URL and Classification)
| LAYER | URL | Score | Blocking Date |
|---|
| EXPOSURE | 94{blocked}.102.63.7/11/files.exe | Virus Accomplice | 5/11/2016 |
| EXPOSURE | mobikash{blocked}..com/language/de-DE/com_loader.exe | Virus Accomplice | 4/27/2016 |
| EXPOSURE | 119{blocked}.17.253.225/ok.jpg | Ransomware, Disease Vector | 5/3/2016 |
| EXPOSURE | Kewix{blocked}.hu:80/ | Ransomware, Disease Vector | 4/6/2016 |
| EXPOSURE | 188{blocked}.225.35.38/farest.555 | Virus Accomplice | 4/2/2016 |
AEGIS Pattern (Behavior Monitoring Pattern)
| LAYER | Detection | Pattern Version | Release Date |
|---|
| DYNAMIC | AN1979T | OPR 1543 | 5/17/2016 |
Network Pattern
| LAYER | Detection | Pattern Version | Release Date |
|---|
| CLEAN-UP | UDP_RANSOM_CERBER_REQUEST | 1.10159.00 | 5/24/2016 |
Make sure to always use the latest pattern available to detect the old and new variants of Ransom_CERBER.
Solution Map - What should customers do?
| Major Products | Versions | Virus Pattern | Behavior Monitoring | Web Reputation | DCT Pattern | Antispam Pattern | Network Pattern |
|---|
| OfficeScan | 11 SP1 above | Update Pattern via web console | Turn On Ransomware Protection Feature/Update Pattern via Web console | Enable Web Reputation Service* | Update Pattern via Web console | Not Applicable | Update Pattern via web console |
|---|
| 10.6 and above | Update Pattern via web console |
| Worry Free Business Suite | 9 SP1 above | Turn On Ransomware Protection Feature/Update Pattern via Web console |
|---|
| 8 and above | Update Pattern via Web console | Update Pattern via Web console |
| Hosted |
| Deep Security | 8.0 and above | Not Applicable | Update Pattern via Web console | Not Applicable | Update Pattern via Web console |
|---|
| ScanMail | SMEX 10 and later | Not Applicable | Update Pattern via Web console | Not Applicable |
|---|
| SMD 5 and later |
| InterScan Messaging | IMSVA 8.0 and above |
|---|
| InterScan Web | IWSVA 6.0 and later |
|---|
| Deep Discovery | DDI 3.0 and later | Not Applicable | Update Pattern via web console |
|---|
| DDAN |
| DDEI |
*Refer to the Product Administrator’s Guide on how to enable the Ransomware Protection, Email Reputation and Web Reputation services features.
Recommendations
Threat Report
Blog


