Summary
WORM_QAKBOT or QAKBOT is a multi-component threat that remains prevalent since its first emergence in 2007. It continuously evolved to avoid easy detection on and removal from an infected system.
Early variants of this malware used constant file names which had the string “_qbot” in them. They utilized single layer of encryption for their configuration files. Later variants, however, set the configuration files' attribute to Hidden and used random names for their component files and folders. These also doubled their configuration files' encryption, which made them harder to decrypt and analyze.
QAKBOT's payloads include malware infection and information theft.
For further information on the previous version, WORM_QAKBOT variants that Trend Micro already detects, click here.
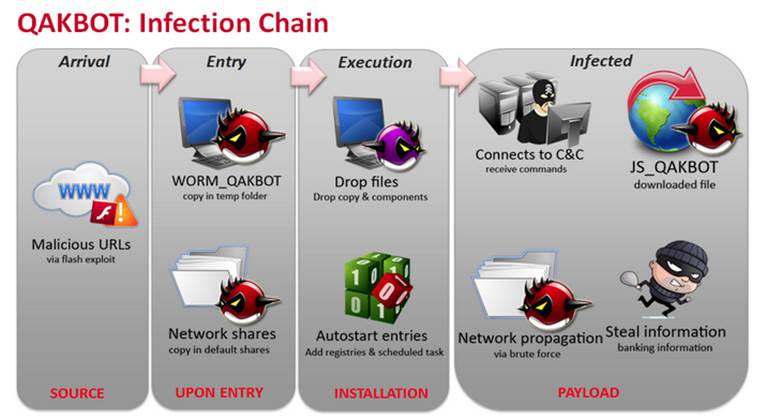
Click image to enlarge.
VSAPI Pattern (Malicious File Detection)
| LAYER | DETECTION | PATTERN VERSION | Release Date |
|---|
| INFECTION | WORM_QAKBOT.SMOT | OPR 12.303 | 1/28/2016 |
| INFECTION | WORM_QAKBOT.SMUW | OPR 12.315 | 2/3/2016 |
| INFECTION | WORM_QAKBOT.SMUV | OPR 12.319 | 2/5/2016 |
| INFECTION | WORM_QAKBOT.SMUX | OPR 12.329 | 2/9/2016 |
| DYNAMIC | JS_QAKBOT.SM1 | OPR 12.313 | 2/2/2016 |
| DYNAMIC | LNK_QAKBOT.SMUV | OPR 12.313 | 2/2/2016 |
| DYNAMIC | Mal_Qakboj | OPT 12.327 | 2/8/2016 |
| DYNAMIC | Mal_QAKBOT-10 | OPR 12.359 | 2/22/2016 |
| INFECTION | SWF_ANGLEREK.C | OPR 12.323 | 2/8/2016 |
WRS Pattern (Malicious URL and Classification)
| LAYER | URL | Score | Blocking Date |
|---|
| CLEAN-UP | aecfdpuspicop{blocked}.biz:443 | DANGEROUS | 2/1/2016 |
| CLEAN-UP | hbjzvgyej{blocked}.org:443 | DANGEROUS | 2/1/2016 |
| CLEAN-UP | xsso{blocked}.aecfdpuspicop.biz | DANGEROUS | 2/1/2016 |
| CLEAN-UP | yrkinsiwejn{blocked}.biz:443 | DANGEROUS | 2/1/2016 |
| CLEAN-UP | yuhjomyygtrbcr{blocked}.info:443 | DANGEROUS | 2/1/2016 |
| CLEAN-UP | xsso{blocked}.hbjzvgyej.org | DANGEROUS | 2/1/2016 |
AEGIS Pattern (Behavior Monitoring Pattern)
| LAYER | Detection | Pattern Version | Release Date |
|---|
| DYNAMIC | 1913T | OPR 1521 | 3/8/2016 |
| DYNAMIC | 1913F | OPR 1519 | 3/1/2016 |
DCT Pattern (System Clean Pattern)
| LAYER | Detection | Pattern Version | Released Date |
|---|
| CLEAN-UP | TSC_GENCLEAN | LATEST DCT OPR | BUILT-IN |
Network Pattern
| LAYER | Detection | Pattern Version | Release Date |
|---|
| CLEAN-UP | HTTP_QAKBOT_REQUEST-8 | RR 1.10149.00 | 7/30/2015 |
| CLEAN-UP | FTP_QAKBOT_REQUEST-2 | RR 1.10103.00 | 1/27/2015 |
Make sure to always use the latest pattern available to detect the old and new variants of WORM_QAKBOT.
Solution Map - What should customers do?
| Major Products | Versions | Virus Pattern | Behavior Monitoring | Web Reputation | DCT Pattern | Network Pattern |
|---|
| OfficeScan | 10.6 and above |
Update Pattern via web console | Update Pattern via web console |
Update Pattern via web console |
Update Pattern via web console | Update Pattern via Web console |
|---|
| Worry Free Business Security | 8.0 and above | Not Applicable |
|---|
| Deep Security | 8.0 and above | Not Applicable | Update Pattern via Web console |
|---|
| InterScan Web | IWSVA 6.0 and later | Not Applicable | Not Applicable | Not Applicable |
|---|
| Deep Discovery | DDI 3.0 and later | Not Applicable | Not Applicable | Update Pattern via web console |
|---|
*Refer to the Product Administrator’s Guide on how to enable the Email Reputation or Web Reputation services features.
Recommendations:
Blog
Threat Report


