Summary
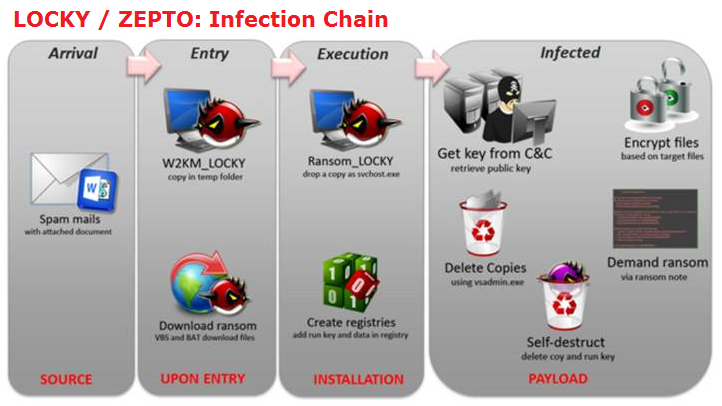
Ransom_LOCKY usually arrives via social engineered spam mails to trick users into clicking the attachment.
No exploit was used in the spam. The user has to click the attachment to initiate the infection chain; which has been observed to contain a DOC file that has a macro code that drops a BAT file when executed. The BAT files also drops a VBS file which downloads this ransomware.
It deletes shadow copies by running vssadmin.exe and adds a run key entry to enable its execution at every system start-up. The run key entry enables the ransomware to continue encrypting files even if interrupted during the previous execution.
The dropped copy, once executed, attempts to retrieve a unique ID, public key and ransom note from the registry. If it fails to retrieve information from the registry, it contacts its C&C server to obtain this specific information and saves it to the registry.
The public key is used for its RSA encryption algorithm.
ZEPTO is known to share technical similarities with LOCKY, especially with spam email-based distribution methods to the use of RSA encryption keys for locking certain file types.
Since LOCKY’s discovery in February 2016, it has continued to evolve and successfully target both individuals and businesses, and has been used in a number of high-profile ransomware attacks on healthcare facilities.
After a binary is downloaded and executed, local files are encrypted and the malware displays a message for the victim demanding payment in Bitcoin. The user receives instruction screens in an .HTML file dropped by the malware, an image file, and a background/wallpaper change. ZEPTO appears to be gaining some traction due to its efficient attack vector—a widespread spam campaign, whereas most ransomware is delivered via other vectors.
Click image to enlarge.
Antispam Pattern
| LAYER | DETAIL | PATTERN VERSION | Release Date |
|---|
| DYNAMIC | Spam Mail with attached document | AS 2146 | 2/21/2016 |
VSAPI Pattern (Malicious File Detection)
| LAYER | DETECTION | PATTERN VERSION | Release Date |
|---|
| INFECTION | HB_LOCKYJ | ENT 12.393.00 | 3/9/2016 |
| INFECTION | HB_LOCKYM | ENT 12.407.00 | 3/15/2016 |
| INFECTION | Ransom_LOCKY.SM | ENT 12.359.00 | 02/24/16 |
| INFECTION | Ransom_LOCKY.SM0 | ENT 12.359.00 | 2/24/2016 |
| INFECTION | Ransom_LOCKY.SM1 | ENT 12.361.00 | 02/25/16 |
| INFECTION | Ransom_LOCKY.SM2 | ENT 12.361.00 | 02/25/16 |
| INFECTION | W2KM_LOCKY.A | ENT 12.349.00 | 02/17/16 |
| INFECTION | X2KM_LOCKY.A | ENT 12.351.00 | 02/18/16 |
| INFECTION | JS_LOCKY.A | ENT 12.353.00 | 02/18/16 |
| INFECTION | RANSOM_LOCKY.DLDSW | ENT 12.637.00 | 7/8/2016 |
WRS Pattern (Malicious URL and Classification)
| LAYER | URL | CATEGORY | Blocking Date |
|---|
| INFECTION | ecoledecorroy{blocked}.be/1/1.exe | Virus Accomplice | 2/19/2016 |
| INFECTION | ratgeber-beziehung{blocked}.de/5/5.exe | Virus Accomplice | 2/19/2016 |
| INFECTION | luigicalabrese{blocked}.it/7/7.exe | Virus Accomplice | 2/19/2016 |
| INFECTION | animar{blocked}.net.pl/3/3.exe | Virus Accomplice | 2/19/2016 |
| CLEAN-UP | sso{blocked}.anbtr.com/domain/kqlxtqptsmys.in | Ransomware | 2/20/2016 |
| CLEAN-UP | xsso{blocked}.kqlxtqptsmys.in/c43344d5351f579349b5f90e1a038859 | Ransomware | 2/20/2016 |
| CLEAN-UP | pvwinlrmwvccuo{blocked}.eu/main.php | Ransomware | 2/19/2016 |
| CLEAN-UP | wblejsfob{blocked}.pw | Ransomware | 2/20/2016 |
| CLEAN-UP | kqlxtqptsmys{blocked}.in | Ransomware | 2/20/2016 |
| CLEAN-UP | xsso{blocked}.kqlxtqptsmys.in | Ransomware | 2/20/2016 |
| CLEAN-UP | cgavqeodnop{blocked}.it | Ransomware | 2/20/2016 |
| CLEAN-UP | pvwinlrmwvccuo{blocked}.eu | Ransomware | 2/20/2016 |
| CLEAN-UP | kvm17915{blocked}.hv9.ru | Ransomware | 2/20/2016 |
| CLEAN-UP | kqlxtqptsmys{blocked}.in/main.php | Ransomware | 2/20/2016 |
| CLEAN-UP | mondero{blocked}.ru/system/logs/56y4g45gh45h | Disease Vector | 2/19/2016 |
| CLEAN-UP | pvwinlrmwvccuo{blocked}.eu/main.php | Ransomware | 2/20/2016 |
| CLEAN-UP | tcpos.com{blocked}.vn/system/logs/56y4g45gh45h | Ransomware | 2/20/2016 |
| CLEAN-UP | www{blocked}.bag-online.com/system/logs/56y4g45gh45h | Ransomware | 2/20/2016 |
| CLEAN-UP | 31{blocked}.41.47.37/main.php | Ransomware | 2/20/2016 |
| CLEAN-UP | 188{blocked}.138.88.184/main.php | Ransomware | 2/20/2016 |
| CLEAN-UP | 95{blocked}181.171.58 | C&C server | 2/19/2016 |
| CLEAN-UP | 185{blocked}.14.30.97 | C&C server | 2/27/2016 |
| CLEAN-UP | 109{blocked}.234.38.35 | Disease Vector | 2/19/2016 |
AEGIS Pattern (Behavior Monitoring Pattern)
| LAYER | DETECTION | PATTERN VERSION | Release Date |
|---|
| DYNAMIC | 1981T | TMTD 1526 | 3/23/2016 |
| DYNAMIC | 1981F | TMTD 1529 | 4/5/2016 |
| DYNAMIC | 1980T | TMTD 1526 | 3/23/2016 |
| DYNAMIC | 1980F | TMTD 1529 | 4/5/2016 |
| DYNAMIC | 1856T | OPR 1483 | 10/6/2015 |
| DYNAMIC | RAN2013T | OPR 1565 | 7/21/2016 |
| DYNAMIC | RAN4705T | OPR 1581 | 9/1/2016 |
DCT Pattern (System Clean Pattern)
| LAYER | DETECTION | PATTERN VERSION | Release Date |
|---|
| CLEANUP | TSC_GENCLEAN | Latest DCT OPR | BUILT-IN |
Network Pattern
| LAYER | DETECTION | PATTERN VERSION | Release Date |
|---|
| CLEANUP | HTTP_RANSOM_LOCKY_REQUEST | RR 1.10151.00 | 3/15/2016 |
Make sure to always use the latest pattern available to detect the old and new variants of Ransom_LOCKY / ZEPTO.
Solution Map - What should customers do?
| Major Products | Versions | Virus Pattern | Behavior Monitoring | Web Reputation | DCT Pattern | Antispam Pattern | Network Pattern |
|---|
| OfficeScan | 11 SP1 above |
Update Pattern via web console
| Turn On Ransomware Protection Feature/Update Pattern via Web console |
Enable Web Reputation Service* |
Update Pattern via Web console
|
Not Applicable
|
Update Pattern via Web console
|
|---|
| 10.6 and above | Update Pattern via web console |
| Worry Free Business Suite | 9 SP1 above | Turn On Ransomware Protection Feature/Update Pattern via Web console |
|---|
| 8 and above |
Update Pattern via web console |
Update Pattern via web console
|
| Hosted Email Security |
| Deep Security | 8.0 and above |
Not Applicable | Update Pattern via web console |
Not Applicable | Update Pattern via Web console |
|---|
| ScanMail | SMEX 10 and later |
Not Applicable |
Update Pattern via Web console |
Not Applicable |
|---|
| SMD 5 and later |
| InterScan Messaging | IMSVA 8.0 and above |
|---|
| InterScan Web | IWSVA 6.0 and later |
|---|
| Deep Discovery | DDI 3.0 and later |
Not Applicable | Update Pattern via web console |
|---|
| DDAN |
| DDEI |
* Refer to the Product Administrator’s Guide on how to enable the Email Reputation or Web Reputation services features.
Recommendations
Threat Report
Blog


