Summary
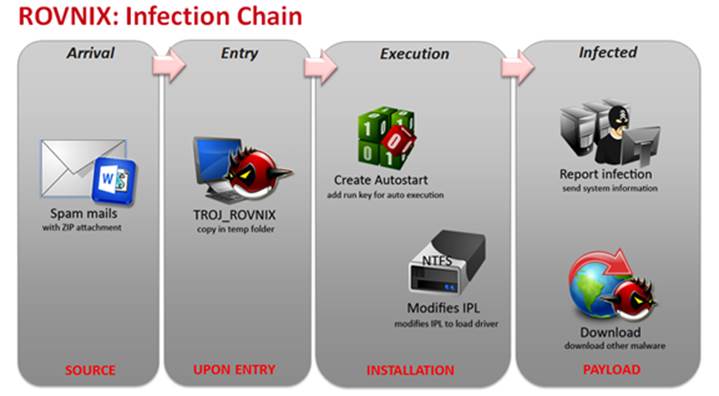
ROVNIX is a Trojan that usually arrives as attachment on spam mails. The spam mail uses social engineering in order to trick the user in opening and executing the attachment.
he attachment is a ZIP archive with the malware file inside. The malware uses at least two extension names: one acting as a decoy, and the other is the actual exe extension. Once user clicks the attachment thru outlook, a copy is created in a randomly-named subdirectory in temporary internet files folder.
The created file remains in that subdirectory even when you exit outlook.exe.
For further information on TROJ_ROVNIX variants that Trend Micro already detects, click here.
Click image to enlarge.
Antispam Pattern
| LAYER | DETAILS | PATTERN VERSION | Release Date |
|---|
| EXPOSURE | Spam mails | AS1060 | 7/6/2015 |
VSAPI Pattern (Malicious File Detection)
| LAYER | DETECTION | PATTERN BRANCH | Release Date |
|---|
| INFECTION | TROJ_ROVNIX.SMW | ENT 10.842.05 | 6/5/2014 |
| INFECTION | TROJ_ROVNIX.SMD | ENT 10.992.06 | 8/18/2014 |
| INFECTION | TROJ_ROVNIX.SME | ENT 10.995.00 | 8/19/2014 |
| INFECTION | TROJ_ROVNIX.SM1 | ENT 11.181.00 | 9/29/2014 |
| INFECTION | TROJ_HPROVNIX.SMA | ENT 12.177.00 | 11/27/2015 |
WRS Pattern (Malicious URL and Classification)
| LAYER | Detection | Classification | Release Date |
|---|
| CLEAN-UP | romnsiebabanahujtr2{blocked}.org | C&C | 1/5/2016 |
| CLEAN-UP | itnhi4vg6cktylw2{blocked}.onion | C&C | 1/5/2016 |
| CLEAN-UP | romnsiebabanahujtr{blocked}.org | C&C | 1/5/2016 |
| CLEAN-UP | romnsiebabanahujtr3{blocked}.org | C&C | 1/5/2016 |
| CLEAN-UP | wujadrin{blocked}.com | C&C | 1/8/2016 |
| CLEAN-UP | toykounn{blocked}.com | C&C | 1/8/2016 |
| CLEAN-UP | lastooooomene2ie2e{blocked}.com | C&C | 1/8/2016 |
| CLEAN-UP | upmisterfliremsnk{blocked}.net | C&C | 1/8/2016 |
| CLEAN-UP | tornishineynarkkek2{blocked}.org | C&C | 1/8/2016 |
AEGIS Pattern (Behavior Monitoring Pattern)
| LAYER | Detection | Pattern Version | Release Date |
|---|
| DYNAMIC | 4158T (terminate) | OPR 1533 | 04/12/2016 |
| DYNAMIC | 4158F (feedback) | OPR 1527 | 03/29/2016 |
| DYNAMIC | 1910T (terminate) | OPR 1521 | 03/08/2016 |
| DYNAMIC | 1910F (feedback) | OPR 1517 | 02/23/2016 |
| DYNAMIC | 4157T (terminate) | OPR 1527 | 03/29/2016 |
| DYNAMIC | 4157F (feedback) | OPR 1523 | 03/15/2016 |
DCT Pattern (System Clean Pattern)
| LAYER | Detection | Pattern Version | Released Date |
|---|
| CLEAN-UP | TSC_GENCLEAN | [existing] | [existing] |
Network Pattern
| LAYER | Detection | Pattern Version | Release Date |
|---|
| CLEAN-UP | HTTP_ROVNIX_REQUEST-4 | RR 1.10143.00 | 01/29/2016 |
| CLEAN-UP | HTTP_ROVNIX_REQUEST-5 | RR 1.10143.00 | 01/29/2016 |
Make sure to always use the latest pattern available to detect the old and new variants of TROJ_ROVNIX.
Solution Map - What should customers do?
| Major Products | Versions | Virus Pattern | Behavior Monitoring | Web Reputation | DCT Pattern | Antispam Pattern | Network Pattern |
|---|
| OfficeScan | 10.6 and above |
Update Pattern via web console |
Update Pattern via web console |
Enable Web Reputation Service* |
Update Pattern via Web console |
Not Applicable | Update Pattern via Web console |
|---|
| Worry Free Business Suite | Standard |
Not Applicable |
|---|
| Advanced/Messaging | Update Pattern via web console |
| Hosted |
| Deep Security | 8.0 and above |
Not Applicable | Update Pattern via Web console | Not Applicable | Update Pattern via Web console |
|---|
| ScanMail | SMEX 10 and later |
Not Applicable |
Update Pattern via Web console |
Not Applicable |
|---|
| SMD 5 and later |
| InterScan Messaging | IMSVA 8.0 and above |
|---|
| InterScan Web | IWSVA 6.0 and later |
|---|
| Deep Discovery | DDI 3.0 and later |
Not Applicable | Update Pattern via web console |
|---|
| DDAN |
| DDEI |
* Refer to the Product Administrator’s Guide on how to enable the Email Reputation or Web Reputation services features.
Recommendations
Blog
Related reports


