Summary
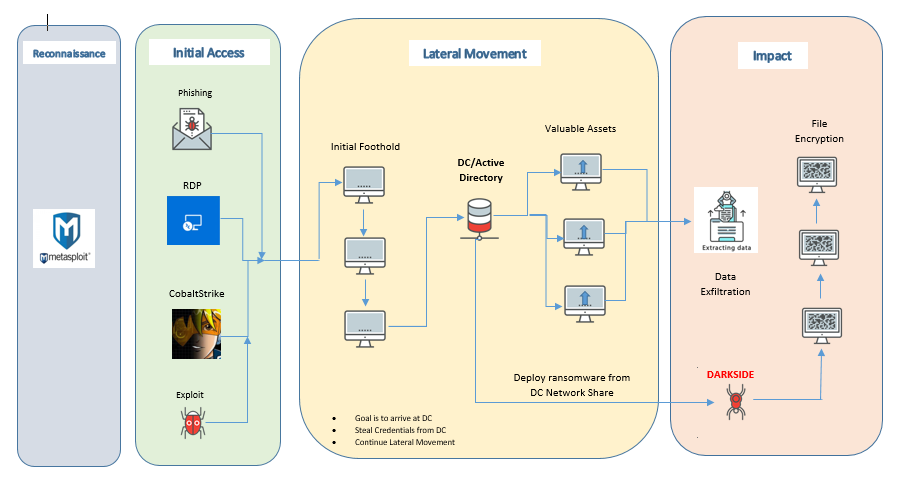
In August 2020, the threat actor group Carbon Spider, associated with the ReVil group, introduced a new ransomware called Darkside. It was later offered as a RaaS in November 2020. It uses a variety of methods to gain initial access to its target system, specifically through phishing, Remote Desktop Protocol (RDP) exploitation, Cobalt Strike, and other exploits. Once it gains a foothold, it moves to the Domain Controller (DC), where it proceeds to steal credentials as well as other valuable assets for data exfiltration. It then continues its lateral movement through the system, eventually using the DC network share to deploy the ransomware to connected machines.
Darkside, which is being offered via the ransomware-as-a-service (RaaS) model, has already been deployed against critical infrastructure in the United States. It uses a “double extortion” technique where the attackers threaten to release sensitive information in addition to encrypting data on their victim's machines.
Capabilities
- File Encryption
- Data Exfiltration
- Command and Control
- Lateral Movement
- Credential Stealing
Impact
- Data loss - loss of important files, documents and other data upon encryption
- Financial loss - users are asked to pay in order to decrypt files that were affected
- Exfiltration of data
Infection Routine
File Reputation
| SHA1 | DETECTION/POLICY/RULES | PATTERN BRANCH/VERSION | RELEASE DATE / LAST UPDATE |
|---|
| a3e7561de73378b453186a6c33858bf47577d69c | Ransom.Win32.DARKSIDE.SMYAAK-B | 16.402.08 | 2020-12-09T19:41:19Z |
| 7ae73b5e1622049380c9b615ce3b7f636665584b | Ransom.Win32.DARKSIDE.SMYAAK-B | 16.402.08 | 2020-12-09T19:41:19Z |
| c104056f9a926d27a2082f0510c97b09cb0eb3e5 | Ransom.Win32.DARKSIDE.SMYAAK-B | 16.402.08 | 2020-12-09T19:41:19Z |
| d1dfe82775c1d698dd7861d6dfa1352a74551d35 | Ransom.Win32.DARKSIDE.YXAH-THA | 16.170.06 | 2020-08-08T10:37:45Z |
Predictive Machine Learning
| DETECTION | PATTERN BRANCH/VERSION |
|---|
| Troj.Win32.TRX.XXPE50FFF036 | In-the-Cloud |
| Troj.Win32.TRX.XXPE50FFF038 | In-the-Cloud |
| Rapid Proliferation | In-the-Cloud |
Behavior Monitoring
| PATTERN BRANCH/VERSION | RELEASE DATE |
|---|
| Malware Behavior Blocking | 2020 |
|
Sandbox Detection
Tipping Point DV filter
| Detection |
|---|
| Malware DV Filter 39754 |
Solution Map - What should customers do?
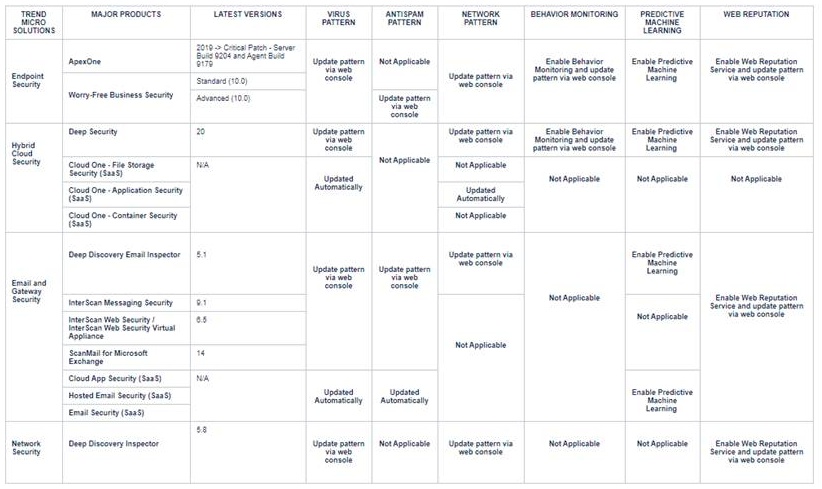
To update Trend Micro products, refer to the corresponding Online Help Center guides.
Recommendation
Make sure to always use the latest pattern available to detect the old and new variants of Darkside Ransomware.
Make sure to implement the ransomware protection features and best practices.
Threat Report


